In the ever-evolving world of cybersecurity, ethical security researchers and penetration testers play a crucial role in safeguarding digital assets. One key aspect of this work involves password cracking, which helps uncover potential weaknesses in authentication systems.
This article will explore the best software tools for password cracking, focusing on their features and effectiveness when used responsibly by authorized security professionals.
By understanding these tools and their capabilities, you can ensure that your organization’s security measures are robust and well-prepared against potential threats.
John the Ripper
John the Ripper is a free and open-source software program designed to help users crack passwords quickly and efficiently. Originally developed in 1996 by Solar Designer, it has since undergone numerous updates and revisions to better meet the needs of modern users. The program is compatible with a wide range of operating systems, including Windows, macOS, Linux, Unix, and more. The tool has gained popularity among security professionals and ethical hackers due to its versatility and ease of use.
Key Features
- Multi-platform compatibility: John can run on various platforms such as Windows/macOS/Linux/Unix
- Flexible configurations: Supports multiple configurations for different use cases.
- Supports different encryption types: It supports various encryption types like MD5, SHA-1/2/3/, Blowfish etc.
- Customizable rulesets: Allows users to create custom rule sets for generating potential passwords combinations
- Automated mode: It automatically selects password cracking modes based on detected encryption types
- Modular design: John’s modular design allows third-party developers to add their own custom plugins
Practical Applications
John the Ripper is suitable for several practical applications:
- Password Recovery: John the Ripper can recover lost passwords for Microsoft Office files, ZIP archives, and other common file formats.
- Security Auditing: It can be used for security auditing by system administrators in detecting weak authentication protocols and vulnerabilities present in their systems.
- Penetration Testing: John the Ripper is an essential tool for penetration testers when attempting to gain access to locked files or systems.
John the Ripper is an excellent password cracking tool that offers several advantages: multi-platform compatibility, flexibility in configurations, support for various encryption types among others.
While it may not be as fast as other software such as Hashcat or as beginner-friendly as Ophcrack, it remains one of the most versatile and powerful tools available for security professionals and ethical hackers alike. Whether you’re trying to recover lost passwords or gain access to locked files, John the Ripper is a reliable choice that won’t disappoint.
Cain & Abel
Cain & Abel is a robust password cracking tool that can be used to recover various passwords using different methods such as brute-force attacks, dictionary attacks, and rainbow table attacks. It was developed by Massimiliano Montoro and released in 2005. Cain & Abel is compatible with Windows operating systems and supports a wide range of protocols such as FTP, HTTP, Telnet, SMB, and many others.
Key Features
- Brute Force Attack: This feature allows users to try out all possible combinations of characters until the correct password is identified.
- Dictionary Attack: This feature uses predefined wordlists to crack passwords faster than brute force.
- Rainbow Table Attack: This attack method utilizes precomputed hashes to quickly crack passwords without needing to run through all possible combinations.
- Sniffer: The sniffer feature allows users to capture network traffic in real-time and extract passwords from it.
- VoIP Sniffer: This feature allows users to capture Voice over Internet Protocol (VoIP) conversations.
Practical Applications
Cain & Abel is mainly used by IT security professionals, penetration testers, and ethical hackers to test the strength of passwords and assess the security of their networks.
It can be used by individuals who have forgotten their passwords or need to recover them from a backup.
Aircrack-ng
Aircrack-ng is an open-source network software suite designed for wireless network security auditing. It was first released in 2006 and has since been used by many security professionals worldwide for various purposes. The primary purpose of Aircrack-ng is to crack WEP and WPA-PSK encryption keys used in Wi-Fi networks.
Key Features
- Wireless Network Scanning – Aircrack-ng can scan wireless networks within range and provide detailed information about them. This feature helps users identify vulnerable networks that could be exploited.
- Brute-Force Attack – Aircrack-ng uses a brute-force attack method to crack passwords by trying different combinations until it finds the correct one. This approach gives Aircrack-ng a high success rate in cracking passwords.
- Wordlist Attack – A wordlist attack involves using a pre-defined list of words to try out different combinations until the correct password is found. This method is more efficient than brute-force attacks when dealing with common passwords.
- Packet Sniffing – Packet sniffing involves capturing packets sent over a network and analyzing them to gather information about the network’s security protocols, weaknesses, and vulnerabilities.
Practical Applications
Aircrack-ng’s primary application is wireless network security auditing. Security professionals can use it to test the security of their organization’s Wi-Fi networks. It can also be used by individuals who have forgotten their Wi-Fi passwords or need to access a protected network for legitimate reasons. However, the user must obtain permission from the network owner before attempting to access a protected network.
Hashcat
Hashcat is a popular and advanced password cracking tool that has been around since 2005. It is an open-source software that runs on various operating systems such as Windows, Linux, and macOS, making it accessible for all users. Hashcat uses advanced algorithms to crack passwords through brute-force attacks, dictionary attacks, and hybrid attacks.
Key Features
- High-Speed Password Cracking – Hashcat is known for its high-speed password cracking capabilities. It can quickly process a large number of hashes and recover passwords from various sources such as encrypted files and databases.
- Multiple Attack Modes – The software offers multiple attack modes such as brute-force attacks, dictionary attacks, rule-based attacks, and mask attacks. These modes provide flexibility to users to choose the best approach for their password cracking needs.
- Optimized Hardware Support – Hashcat is designed to utilize the full potential of modern CPUs and GPUs. This means that users can take advantage of their hardware capabilities to optimize the speed of password cracking.
- Wide Range of Algorithms Supported – Hashcat supports a wide range of algorithms such as MD5, SHA1, SHA2-256/512, DES, and WPA/WPA2. This means that users can crack passwords from various sources using a single tool.
Practical Applications
Hashcat has various practical applications, including:
- Password Recovery – Hashcat can be used to recover lost or forgotten passwords from encrypted files, databases, and other sources.
- Penetration Testing – Penetration testing is a security assessment that involves testing the security of a system by simulating an attack. Hashcat can be used as a tool in penetration testing to ensure that the system is secure.
- Cybercrime Investigations – In cases of cybercrime investigations, Hashcat can be used by law enforcement agencies to crack passwords and access data that may otherwise be inaccessible.
Overall, Hashcat is a powerful password cracking tool that offers advanced features for recovering lost or forgotten passwords. Its high-speed capabilities and support for multiple attack modes make it an ideal choice for penetration testers and law enforcement agencies alike.
RainbowCrack
RainbowCrack is a password cracking tool that supports various hash types including MD5, SHA1, LM Hash, NTLM Hash, and more. It uses a rainbow table to store hashes that make it faster than traditional brute-force methods.
Some of the key features of RainbowCrack include:
- Multi-platform support: RainbowCrack runs on multiple platforms including Windows, Linux, and macOS.
- Pre-computed tables: The tool uses pre-computed tables that make it faster than traditional brute-force methods.
- Support for multiple hash types: Supports various hash types including MD5, SHA1, LM Hash, NTLM Hash among others.
- Customizable rainbow tables: Users can create custom rainbow tables based on their requirements.
Practical Applications
Password cracking tools like RainbowCrack can be used to recover lost passwords or to test the strength of a system’s password security. Governments, law enforcement agencies, and network administrators also use tools like this to assess their systems’ vulnerabilities.
In summary, RainbowCrack is a powerful password cracking tool that offers various features that cater to users’ requirements. Its speed and multiple platform support make it a popular choice among users. However, it requires significant computing power to function optimally and has limited language support.
THC Hydra
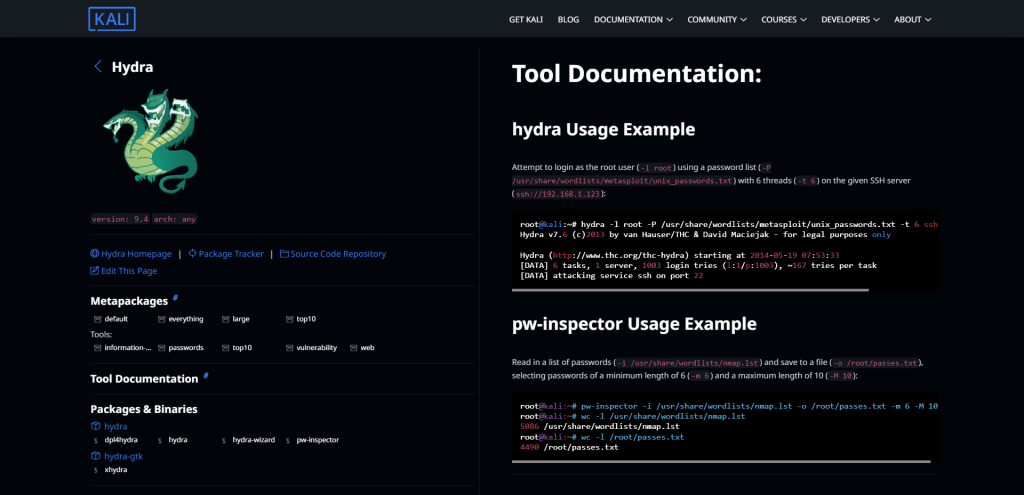
THC Hydra is an open-source software application that is widely used for password cracking. The software is compatible with different operating systems and can be used to crack passwords of various protocols, including FTP, HTTP, HTTPS, IMAP, LDAP, MS-SQL, MySQL, PostgreSQL, RDP, SSHv2, SMB and Telnet.
Key Features
- Multi-Protocol Support – as mentioned above, THC Hydra supports different protocols.
- Parallelized Attack – THC Hydra is designed to perform parallelized attacks on multiple login pairs simultaneously.
- Multi-Threaded – the software is multi-threaded to ensure efficient use of resources in performing an attack.
- Brute Force and Dictionary Attacks – these are the two main types of attacks used by the software.
- User-Friendly Interface – THC Hydra comes with an easy-to-use interface that makes it user-friendly for both beginners and advanced users.
Practical Applications
The primary use of THC Hydra is for password cracking purposes. This includes both ethical and unethical applications.
Ethical applications include:
- Network and system administrators can use the software to test the strength of their passwords and identify vulnerabilities in their systems.
- Penetration testers can use it as part of their security testing procedures.
Unethical applications include:
- Hackers can use THC Hydra to break into systems and steal sensitive information illicitly.
- Cybercriminals can exploit the software to gain unauthorized access to different networks or services.
Overall, THC Hydra remains one of the most popular password cracking tools in the market due to its versatility and effectiveness in recovering passwords from various protocols. While it has its limitations and legal considerations, it remains a valuable tool for network administrators and cybersecurity experts seeking to identify system weaknesses before malicious actors do.
As always, remember when using any hacking tool including THC Hydra, ensure compliance with ethical standards and always obtain explicit permission before performing any tests on systems you do not own.
Ophcrack

Ophcrack is a free and open-source password cracking software that is designed to crack Windows passwords. The software uses rainbow tables to crack passwords and supports many different operating systems such as Windows XP, Vista, 7, and 8. Its user-friendly interface makes it easy for both novice and advanced users.
Key Features
- Free and open-source
- Supports Windows XP, Vista, 7, and 8
- Uses rainbow tables to crack passwords
- User-friendly interface
- LiveCD available for download
Practical Applications
Ophcrack is mainly used for password recovery purposes. It can be used to retrieve forgotten passwords, especially for Windows operating systems. The software can also be used by system administrators to reset passwords for user accounts.
L0phtCrack
L0phtCrack is a password auditing and recovery tool developed by L0pht Heavy Industries. It is primarily used by network administrators, IT professionals, and security analysts to detect weak passwords on local or remote systems. The software uses various methods, including brute force attacks and dictionary attacks, to uncover passwords for user accounts on Windows systems.
Key Features
- Multiple Attack Types – L0phtCrack supports various attack types such as brute force attacks, dictionary attacks and hybrid attacks. It also enables customization of attack parameters based on user preferences.
- Real-time Password Cracking – This software features real-time password cracking that allows users to monitor the progress of any attack in real time.
- Reporting and Analysis Tools – L0phtCrack generates detailed reports on password strengths and vulnerabilities which are then categorized according to risk levels.
- Password Complexity Checks – The tool has built-in testing capabilities that determine the complexity of passwords by testing them against commonly used lists of words or phrases.
Practical Applications
L0phtCrack is an ideal tool for network administrators and security analysts who want to test the strength of passwords on their systems. It can also be used by individuals who want to audit their own passwords to ensure they are secure enough. The software can help identify weak passwords that could be exploited by hackers to gain unauthorized access.
While mastering all its features may take some time, its intuitive interface makes it easy to use for both beginners and experts alike. Hence, if you are looking for a reliable solution for password cracking purposes or simply want to audit your own passwords for potential weaknesses, L0phtCrack is definitely worth considering.
Summary
Throughout this article, we have explored various reputable password cracking software tools, each with its unique features and capabilities. By employing these tools responsibly and within legal boundaries, security professionals can gain valuable insights into potential weaknesses and take corrective action.
Ultimately, the careful application of these tools contributes to a safer digital landscape and helps organizations safeguard their sensitive information from malicious threats.













