Update: Both Cloudflare and Namecheap have taken drastic actions to discourage the spread of malware by the Poyfill.io domain name. Read more here.
A major supply chain attack involving the popular JavaScript library Polyfill has affected over 110,000 websites, including high-profile users such as JSTOR, Intuit, and the World Economic Forum. The incident, discovered on June 25, 2024, stems from a change in ownership of the Polyfill project earlier this year.
Polyfill is an open-source library designed to support older browsers by dynamically generating code based on HTTP headers. In February 2024, a Chinese company called Funnull acquired the polyfill.io domain and associated GitHub account. Since then, the new owners have been injecting malware into sites that embed the library via cdn.polyfill.io.
The malicious malware code embedded in the hijacked library redirects users to fraudulent sites, bookmakers, and online casinos.
Security research firm Sansec decoded one variant of the malware, revealing its nature:
- It redirects mobile users to sports betting sites using a fake Google Analytics domain (www.googie-anaiytics.com).
- The code only activates on specific mobile devices at certain hours.
- It avoids activation when detecting an admin user.
- Execution is delayed when web analytics services are detected, presumably to avoid appearing in statistics.
The malicious code is dynamically generated based on HTTP headers, suggesting multiple attack vectors are likely in use.
In response to the attack, Google has automatically suspended Ads accounts linked to the ‘googie-analytics’ redirect. Some reports indicate that this has been happening since at least June 15.
The new owner is removing any complaints on GitHub that mention suspicious activity or changes in ownership, apparently expecting users to believe that the original website creators initiated the automatic transition.
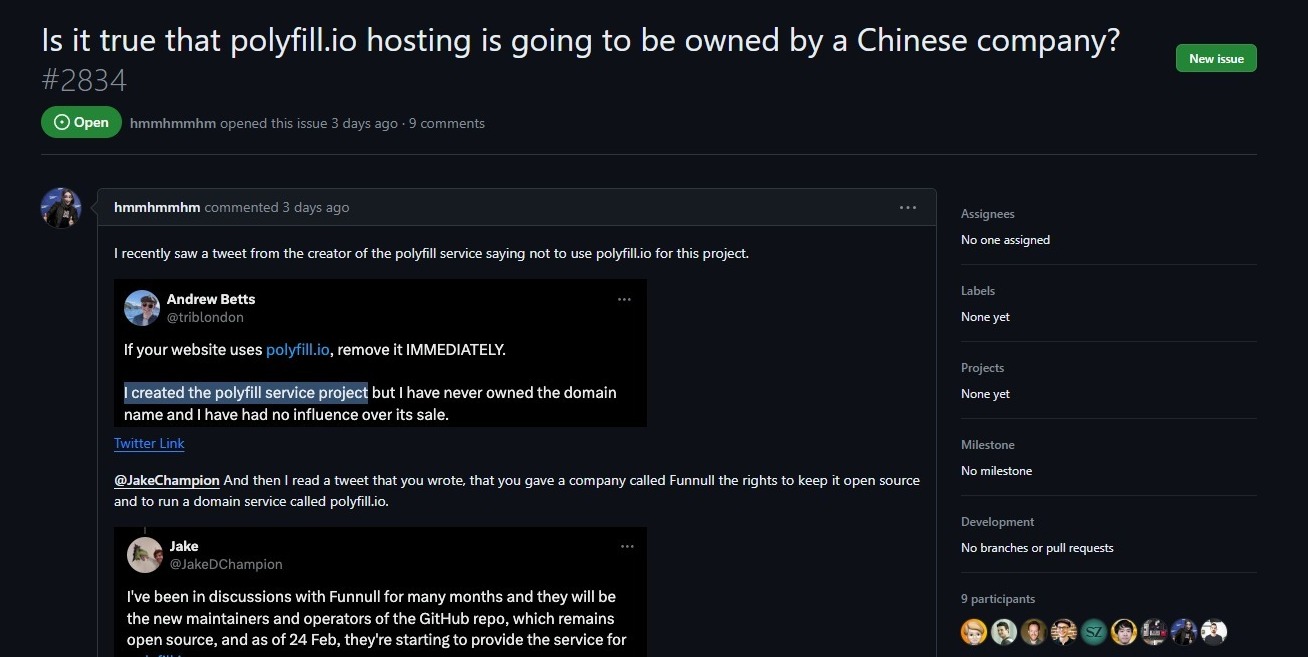
Andrew Betts, the original creator of Polyfill, recommends abandoning the library entirely, stating that modern browsers no longer require it. Trusted alternatives are available from Fastly and Cloudflare for those needing similar functionality.
No website today requires any of the polyfills in the polyfill.io library. Most features added to the web platform are quickly adopted by all major browsers, with some exceptions that generally can’t be polyfilled anyway, like Web Serial and Web Bluetooth.
Andrew Betts
Those still requiring Polyfill’s functionality have several options:
- Use the alternatives provided by Fastly or Cloudflare.
- Host a local copy based on the code from a forked repository created by the original project author.
- Consider updating their sites to no longer require compatibility layers for older browsers.
The takeaway here for developers is pretty straightforward: always keep a close eye on the third-party libraries you use. This incident shows how messy things can get when a project changes hands. Regularly check and update your dependencies to safeguard your projects from similar risks.
