A port is a communication endpoint used in computer networking. It allows computers to exchange data with each other over a network connection. A computer can have many ports; each assigned a unique number that identifies its purpose.
An open port is a port that is currently accepting incoming connections from the network. This means that there is an active service or application listening on that port and waiting for requests to be sent to it.
Computers have ports so that they can communicate with other devices over a network. However, leaving open ports unsecured can put your computer and network at risk of unauthorized access and security breaches.
Why should you scan for open ports?
Open ports are like unlocked doors on a house. They provide an entry point for attackers to access your network and potentially compromise your sensitive data or systems. Scanning for open ports can help identify these vulnerabilities, so they can be secured before an attacker exploits them.
By regularly scanning for open ports, you can improve your network security by identifying potential entry points that need to be secured. This proactive approach can help prevent security breaches and protect your organization’s assets.
How can you scan for open ports?
Scanning for open ports involves searching for any accessible ports on a network or device that could be exploited by a hacker. One of the most common methods for scanning open ports is using specialized software tools known as port scanners.
Port scanners work by sending packets of data to different ports on a target system and analyzing the response to determine if the port is open, closed, or filtered. Port scanners can be used both manually and automatically, and they can scan both local and remote networks.
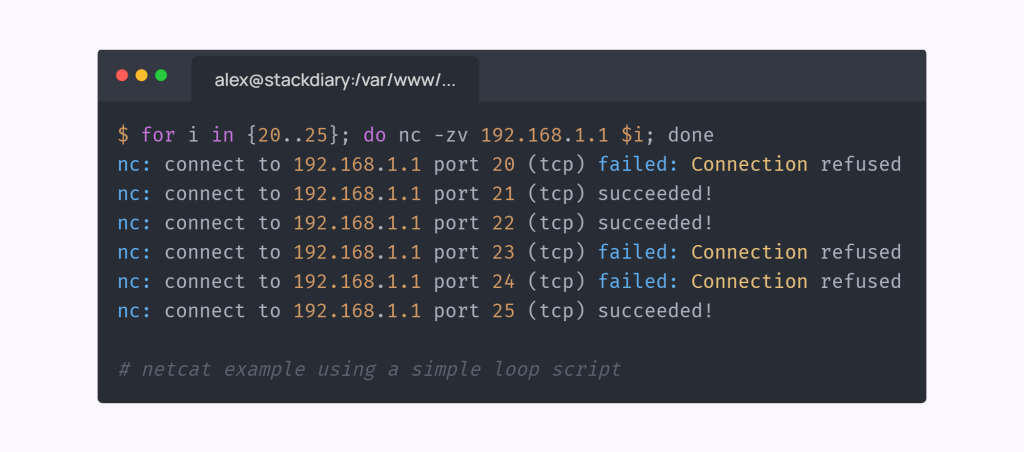
There are several types of port scanning techniques, including full connect scans, stealth scans (also known as half-open or SYN scans), and UDP scans. Each technique has its own advantages and disadvantages depending on the circumstances.
While it is possible to manually scan for open ports by using command-line tools like Telnet or PowerShell, using specialized software tools like Nmap or Angry IP Scanner can make the process faster and more efficient. Those are also the type of tools we’ll be covering in this article!
Nmap
Nmap is a popular open-source tool used for scanning and mapping networks to detect open ports and services running on them. It works by sending packets to target hosts and analyzing the responses received to determine if a particular port is open or closed. Nmap offers a wide range of features that can enhance scanning and security efforts, such as flexible target specification, OS detection, version detection, scriptable interaction with the target, and advanced output options. It can also detect hidden or stealthy services on an endpoint.
Nmap can be operated via command-line interface or GUI (via Zenmap), making it accessible to a broad audience of users. Zenmap is a graphical user interface for Nmap that provides an easier way to operate Nmap without having to remember complex commands or configurations. It offers many of the same features as Nmap’s CLI version but presents them in an easier-to-use format.
What features does Nmap offer?
It offers a wide range of features to enhance scanning and security efforts, including the ability to perform version detection, OS detection, and scriptable interaction with target systems. Nmap also supports various scanning techniques such as TCP SYN scan, TCP connect scan, UDP scan, and more.
It can even detect hidden or stealthy services on an endpoint by using advanced scanning techniques like fragmentation or idle scanning.
Can Nmap detect hidden or stealthy services on an endpoint?
Yes! Nmap accomplishes this by using various advanced techniques such as TCP/IP stack fingerprinting, idle scanning, and service version detection. These methods allow Nmap to identify even those services that are designed to avoid detection through stealth techniques.
Additionally, Nmap provides a scripting engine that allows users to customize and extend its functionality.
Angry IP Scanner
Angry IP Scanner is a popular open-source network scanning tool that allows users to scan IP addresses and ports to identify potential security vulnerabilities. One advantage of Angry IP Scanner is its speed, as it can scan large networks quickly. This tool also offers various advanced features, including the ability to resolve hostnames, scan for NetBIOS names, and search for open ports on a range of protocols.
Users may choose Angry IP Scanner over other tools for its simplicity and ease of use, as it does not require advanced technical knowledge. Additionally, this tool can be used in tandem with other network security products to provide additional layers of protection.
Angry IP Scanner provides detailed reporting and logging options that enable users to review the results of the scan in a user-friendly format. However, there may be some risks associated with scanning for open ports, such as potential false positives or system disruptions. Therefore, it is recommended to use this tool cautiously and only on networks that you have permission to access.
Does Angry IP Scanner provide detailed reporting or log output options?
Angry IP Scanner can be used in conjunction with other network security products, and it provides various output options, including detailed reporting and logging capabilities, which can be useful when conducting vulnerability assessments or performing forensic investigations.
Fing
Fing is a free network scanning tool that allows users to scan a network and discover all connected devices, their IP addresses, MAC addresses, and even operating systems. It can be used to detect open ports on devices as well as identify potential security vulnerabilities.
One unique feature of Fing is its ability to detect all devices on a Wi-Fi network, including those not connected via Ethernet cable. This makes it an excellent tool for securing wireless networks.
Fing also offers privacy features such as masking the MAC address of the scanning device and encrypting scan results, which may be useful when scanning networks.
How does Fing differ from other tools mentioned?
Unlike some of the other tools mentioned in this article, Fing is not primarily focused on identifying open ports or vulnerabilities. Instead, it helps users to quickly discover all devices connected to a network, including those connected via Wi-Fi or Ethernet cables.
Fing offers several privacy features that may be useful when scanning networks, including the ability to anonymize device names and MAC addresses. This can help users ensure that sensitive information is not being shared when conducting network scans.
Can it detect devices on a Wi-Fi network as well as devices connected via Ethernet cable?
Fing is a network scanner that can detect devices on both Wi-Fi and Ethernet networks. This makes it a useful tool for scanning and securing your network from open port vulnerabilities on all types of devices.
Does Fing offer any privacy features that may be useful when scanning networks?
Fing offers several privacy features, including the option to hide your device from the network scan and the ability to disable probe requests for Wi-Fi networks. These privacy features may be useful for individuals or businesses concerned about security or privacy when scanning their networks.
OpenVAS
OpenVAS is a free and open-source vulnerability scanner that can detect security holes in a network. It is designed to be highly modular, making it easy for users to customize and extend the functionality of the tool. OpenVAS differs from other scanning tools in that it can not only detect open ports, but also other vulnerabilities like misconfigured services, weak passwords, and outdated software.
In addition to its core scanning capabilities, OpenVAS also provides advanced features like centralized management of multiple scanners and integration with various third-party tools. It has support for a range of operating systems including Linux, Windows, and macOS.
OpenVAS provides detailed reporting options with an XML-based output format that can be easily parsed by other tools for further analysis. It also allows users to configure different scan types according to their needs.
How does OpenVAS differ from other scanning tools?
OpenVAS is a network vulnerability scanner that differs from other scanning tools in a few ways. Firstly, it is open-source software with a community of contributors continually updating and improving the tool. Additionally, OpenVAS can detect vulnerabilities beyond just open ports, including misconfigurations, weak passwords, and outdated software.
OpenVAS also has the ability to integrate with other security solutions or management consoles, making it a flexible choice for network security teams. Overall, OpenVAS provides a comprehensive and customizable approach to scanning for vulnerabilities in your network.
What types of vulnerabilities can it detect besides open ports?
Aside from detecting open ports, it also has the ability to detect other types of vulnerabilities, such as misconfigured services, weak passwords, and software vulnerabilities. OpenVAS is known for its comprehensive vulnerability scanning capabilities and can be integrated with other security solutions or management consoles to improve overall network security.
With OpenVAS, users can get detailed reports and insights into their network’s security posture, making it an essential tool for IT professionals looking to secure their networks against cyber threats.
Nessus

Nessus is a popular vulnerability scanner that helps identify vulnerabilities, misconfigurations, and malware on a network. It is widely used by security professionals to audit and assess the security posture of various organizations.
Some of the key features of Nessus include its ability to scan for known vulnerabilities in operating systems, applications, and network devices. It also offers compliance checks against industry standards such as PCI DSS and HIPAA. Nessus provides detailed report generation capabilities including custom reports that can be tailored to meet specific requirements.
What are the key features of Nessus?
Nessus is a powerful vulnerability scanner that can identify security vulnerabilities in a network. It offers a range of features to enhance scanning and security efforts, including:
- Comprehensive vulnerability scanning: Nessus can scan both local and remote hosts to identify vulnerabilities across a wide range of platforms, devices, and applications.
- Easy-to-use interface: Nessus has a user-friendly interface that allows users to quickly set up and run scans.
- Customizable reporting: Nessus generates detailed reports that include information on detected vulnerabilities, severity levels, risk factors, and remediation recommendations. Reports can be customized based on specific requirements or compliance standards.
- Integration with other security tools: Nessus can integrate with other security solutions or management consoles for improved threat intelligence sharing and incident response.
- Continuous monitoring: Nessus can perform regular scans to detect new vulnerabilities as they emerge, helping organizations stay ahead of potential threats.
- Cloud-based deployment option: Nessus can be deployed in cloud environments for easy scalability and flexibility.
Overall, Nessus is an effective tool for identifying and managing network vulnerabilities, making it a popular choice among IT professionals for enhancing network security.
Summary
In conclusion, selecting the right tools to scan for open ports and secure your network is a vital step towards ensuring the safety and reliability of your online infrastructure. With a variety of options available, it’s important to consider each tool’s features, ease of use, compatibility, and effectiveness in identifying vulnerabilities and potential threats.
Keep in mind that the ideal tool for one individual or organization may not necessarily be the best choice for another. It’s essential to thoroughly assess your network environment, security needs, and the level of expertise required. Don’t be reluctant to explore multiple tools, as finding the perfect solution may involve some trial and error.
By opting for a tool that aligns with your network security requirements, you’ll be well-equipped to safeguard your digital assets, maintain privacy, and protect against cyber threats. We hope this article has provided you with valuable insights and guidance as you explore various tools to scan for open ports and secure your network.













