According to researchers, VPN users worldwide are at risk from a newly identified vulnerability known as the “port shadow” attack. This flaw, which affects widely used VPN software such as OpenVPN, WireGuard, and OpenConnect, enables attackers to eavesdrop on connections, hijack data streams, and even redirect users to malicious websites.
Benjamin Mixon-Baca, a former fellow at the Citizen Lab Open Technology Fund (OTF) Information Controls Fellowship Program, and co-authors, including Citizen Lab researcher Jeffrey Knockel, uncovered the vulnerability. Their study, presented at the Privacy Enhancing Technologies Symposium (PETS) 2024, explores the connection tracking frameworks used by major operating systems to manage VPN traffic.
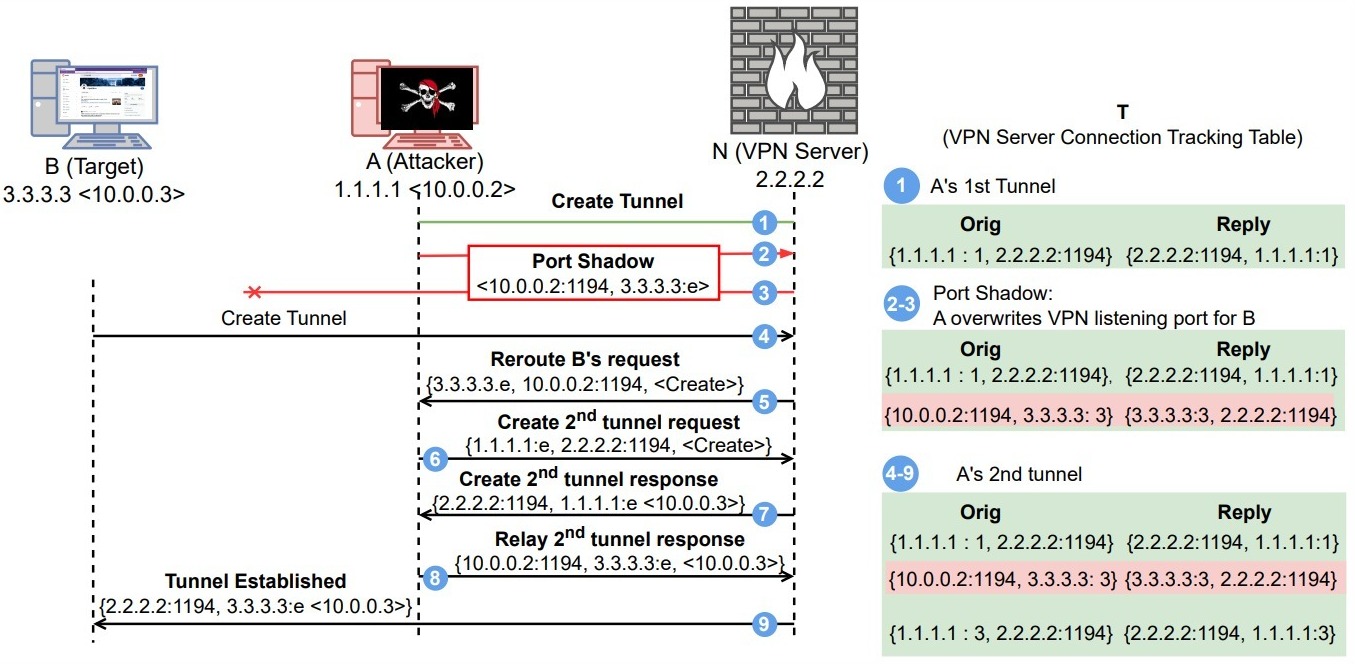
The connection tracking framework is at the heart of the port shadow attack, a system that directs traffic between VPN clients and servers. This framework, shared among all users connected to the same VPN server, can be manipulated by a malicious actor to reroute packets, effectively intercepting and redirecting a user’s data.
“We call this attack a port shadow because the attacker shadows their own information as a shared resource on the victim’s port,” explain the researchers. This method enables attackers to conduct port scans, hijack sessions, and snoop on unencrypted data, all while maintaining a position as a network router between the target and the VPN server.
The researchers found that the vulnerability affects VPN implementations on Linux and FreeBSD, with Linux systems using Netfilter being particularly susceptible. FreeBSD, while less vulnerable, is not entirely immune to the most severe forms of the attack.
“Our findings show that VPN software, which is intended to enhance security and privacy, can, in fact, make users more vulnerable,” the study notes. This is a significant concern, especially for at-risk groups such as dissidents, journalists, and NGOs, who rely on VPNs to protect their communications from surveillance and censorship.
While a comprehensive fix for the vulnerability is not yet available, the researchers offer several mitigation strategies. VPN providers are advised to implement specific firewall rules to block the attack. For instance, on Linux systems, the following IPtables command can help:
# iptables -t nat -A POSTROUTING -p udp -o enp0s8 --sport 1194 -j SNAT --to-source 192.168.2.254:32768-60999Additionally, end users are encouraged to use alternative protocols, such as ShadowSocks or Tor, which do not rely on the vulnerable connection tracking framework. “Users should connect to private VPN servers or switch to non-vulnerable protocols to ensure their safety,” the researchers recommend.
Interestingly, this issue was previously identified in 2022 and assigned CVE number CVE-2021-3773, with a severity rating of 9.8 out of 10. Some VPN services, including NordVPN, ExpressVPN, and Surfshark, were found to be not vulnerable to this specific issue.
