A widespread supply chain attack involving the Polyfill.io service has led to swift action from major internet infrastructure providers. Over 110,000 websites using Polyfill.io have been impacted after a Chinese company called Funnull acquired the service earlier this year.
Polyfill.io, a Content Delivery Network (CDN) that provides JavaScript code to enable modern functionality on older browsers, became a vector for malware distribution under its new ownership. On June 25, security researchers at Sansec uncovered that Funnull had been injecting malicious code targeting mobile devices through any site embedding cdn.polyfill.io.
The malware embedded in the compromised library redirects mobile users to a sports betting site using a fake Google Analytics domain, activates only on specific devices at certain hours, and employs various techniques to evade detection and reverse engineering.
Cloudflare and Namecheap take a stand
In response to these findings and the community involvement, Namecheap, the domain’s registrar, has taken decisive action by making the Polyfill.io domain unavailable.
Cloudflare has also stepped in to address the security threat. They’ve created a secure mirror of the Polyfill service under their cdnjs domain and implemented an automatic URL rewriting feature for any site using Cloudflare services.
This feature, now active by default for free plan users and available with a single click for paid customers, automatically redirects any polyfill.io links to Cloudflare’s secure mirror. The company is urging all website owners, regardless of whether they use Cloudflare, to replace polyfill.io links with their mirror at cdnjs.cloudflare.com/polyfill/.
We have taken the exceptional step of using our ability to modify HTML on the fly to replace references to the polyfill.io CDN in our customers’ websites with links to our own, safe, mirror created back in February.
Cloudflare
Cloudflare’s solution offers a non-breaking change, serving the same polyfill content while mitigating the risk of supply chain attacks. Additionally, Fastly, another major CDN provider, has created its own open-source fork of the Polyfill service, providing website owners with multiple trusted alternatives.
The incident has affected high-profile users, including Atlassian, Square, Sendgrid, JSTOR, and even government websites. Google has been proactively warning site owners about compromised landing pages related to this attack.
Industry experts, including Andrew Betts, the creator of the original Polyfill Service Project, had been sounding alarms about the change in ownership since February. Betts urged website owners to remove Polyfill.io immediately, stating that most modern websites no longer require these polyfills.
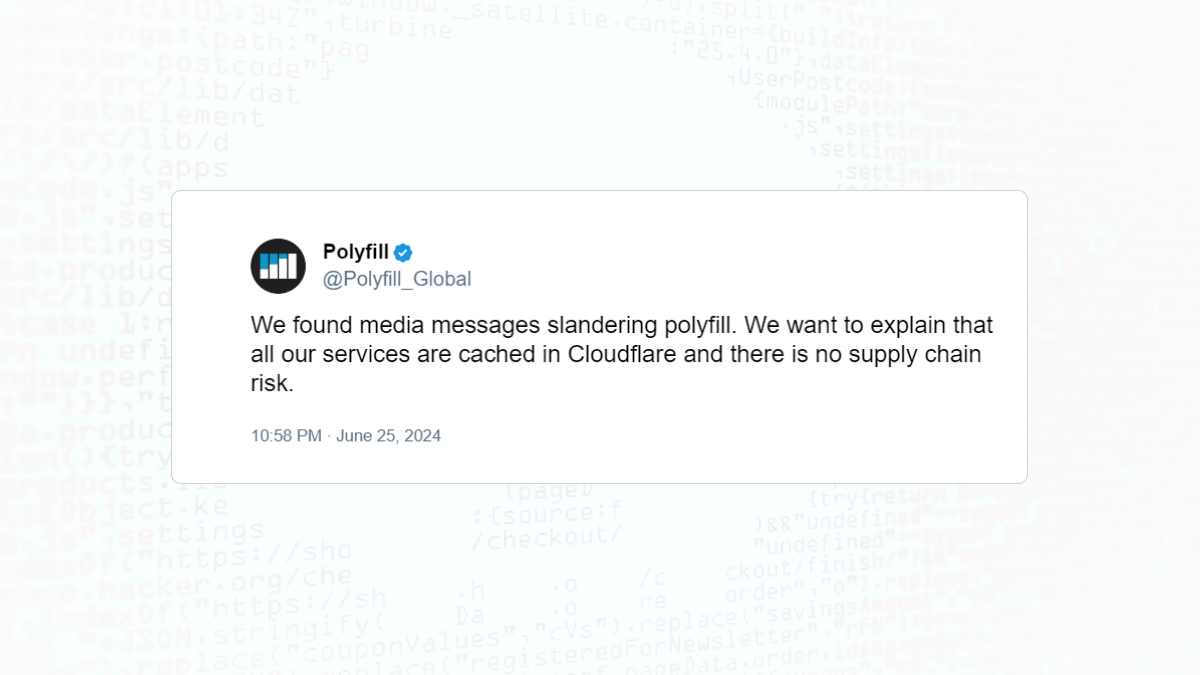
Despite mounting evidence, Funnull has denied “accusations” of a supply chain attack, claiming their services are cached in Cloudflare and that they wouldn’t risk their reputation. They’ve relaunched their service on a new domain, polyfill.com, but given the circumstances, you should avoid it like the plague.
The popular content blocker uBlock Origin has also taken action. On June 26, a pull request was merged, adding polyfill.io and its subdomains to the badware.txt file. This means that uBlock Origin users trying to visit the Polyfill.io domain would get a warning, and the script itself would be prevented from loading on any affected pages.
Let’s be clear, too: this could have been prevented.
Self-hosting the Polyfill service, rather than relying on a third-party CDN, would have shielded websites from this supply chain attack. By maintaining control over the code and its delivery, organizations could have ensured its integrity and avoided the risks associated with external services changing hands or being compromised.
While self-hosting requires more maintenance, it offers greater security and stability, especially for critical web applications. This incident is a reminder of the trade-offs between convenience and security when integrating third-party services.
The history of Polyfill
Polyfill.js was created by the Financial Times development team about 15 years ago. This JavaScript library was designed to make web applications work with older browsers by providing modern features they lacked. Developers could use the latest standards while maintaining compatibility across different browser versions.
Initially hosted on polyfill.io, the library became widely used. However, its ownership changed hands on February 24, 2024, when Jake Champion, a former FT engineer, transferred the domain and GitHub repository to Funnull. Champion, now employed by Fastly, has since made his Twitter account private following community backlash.
