A critical vulnerability in GitLab, CVE-2024-5655, has been disclosed, enabling attackers to run pipeline jobs under any user account. This vulnerability, present since GitLab version 15.8, poses significant risks to internal repositories and private projects across both GitLab Community Edition (CE) and Enterprise Edition (EE). To mitigate the threat, GitLab urges immediate updates to versions 17.1.1, 17.0.3, and 16.11.5.
To run pipelines as any user means that due to the vulnerability, someone could execute automated tasks (jobs) in the development process as if they were another user.
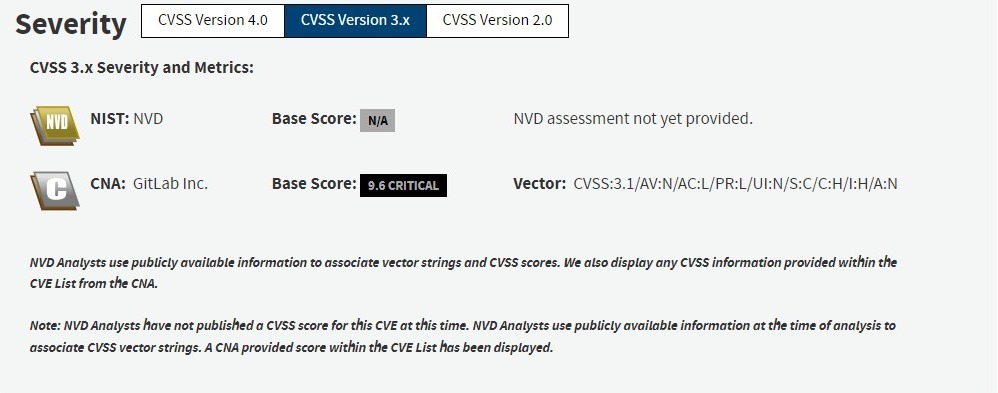
The vulnerability was disclosed on June 26, when GitLab released a series of updates addressing 14 vulnerabilities, including the critical CVE-2024-5655, which has a severity rating of 9.6 out of 10 on the CVSS scale.
This issue was discovered through GitLab’s partnership with HackerOne, a platform that facilitates vulnerability bounty programs.
Nikhil George, a Senior Security Engineer at GitLab, emphasized the gravity of this vulnerability:
This issue allows jobs in the CI pipeline to be run under arbitrary user contexts, which could lead to unauthorized access and potential data leaks. While we have not found evidence of exploitation on our managed platforms, the risk remains significant for self-hosted instances.
Nikhil George
GitLab has implemented several breaking changes in response to this vulnerability. Notably, the merge request (MR) re-targeting workflow has been altered, requiring manual pipeline starts when a target branch is merged. Additionally, GraphQL authentication using CI_JOB_TOKEN has been disabled by default from version 17.0.0, further tightening security.
To mitigate the risks associated with this vulnerability, GitLab strongly recommends the following actions:
- Immediate Update: Upgrade to the latest versions—17.1.1, 17.0.3, or 16.11.5—depending on your current installation.
- Manual Pipeline Execution: Adjust workflows to accommodate the new requirement for manually starting pipelines after MR re-targeting.
- Review Token Configurations: Ensure GraphQL API access is configured with supported authentication tokens, as CI_JOB_TOKEN is now disabled by default.
Additionally, organizations should review their overall security practices and ensure that all GitLab instances are consistently updated and configured following best security practices.
