Gogs, a popular open-source solution for self-hosting Git repositories, has been scrutinized for its prolonged inaction on reported security issues. According to researchers Thomas Chauchefoin and Paul Gerste from Sonar, Gogs has failed to address four critical vulnerabilities for over a year.
Gogs is highly regarded in the developer community, with over 44,000 stars on GitHub and over 90 million Docker image downloads. It is a widely used platform for source code management. However, Chauchefoin and Gerste’s findings, detailed in a recent blog post, reveal that the platform is vulnerable to severe attacks that can compromise source code, insert malicious backdoors, or wipe entire codebases.
The researchers discovered four unfixed vulnerabilities in Gogs:
- Argument Injection in the built-in SSH server
- Argument Injection when tagging new releases
- Argument Injection during changes preview
- Deletion of internal files
Despite their efforts to responsibly disclose these issues to the Gogs maintainers, including providing detailed reports and recommended fixes, the vulnerabilities remain unpatched in the latest release of Gogs (version 0.13.0).
These vulnerabilities allow authenticated attackers to execute arbitrary commands on the Gogs server, read and modify source code, and access sensitive configuration files. The first vulnerability, involving argument injection in the built-in SSH server, exemplifies the potential for exploitation. An attacker can manipulate the SSH environment variables to inject commands, gaining control over the server.
Gogs uses the golang.org/x/crypto/ssh package to manage SSH connections, adding its authorization layer. The issue arises in the handling of environment variables. By injecting malicious arguments, attackers can exploit the --split-string option of the env command to execute arbitrary commands on the server.
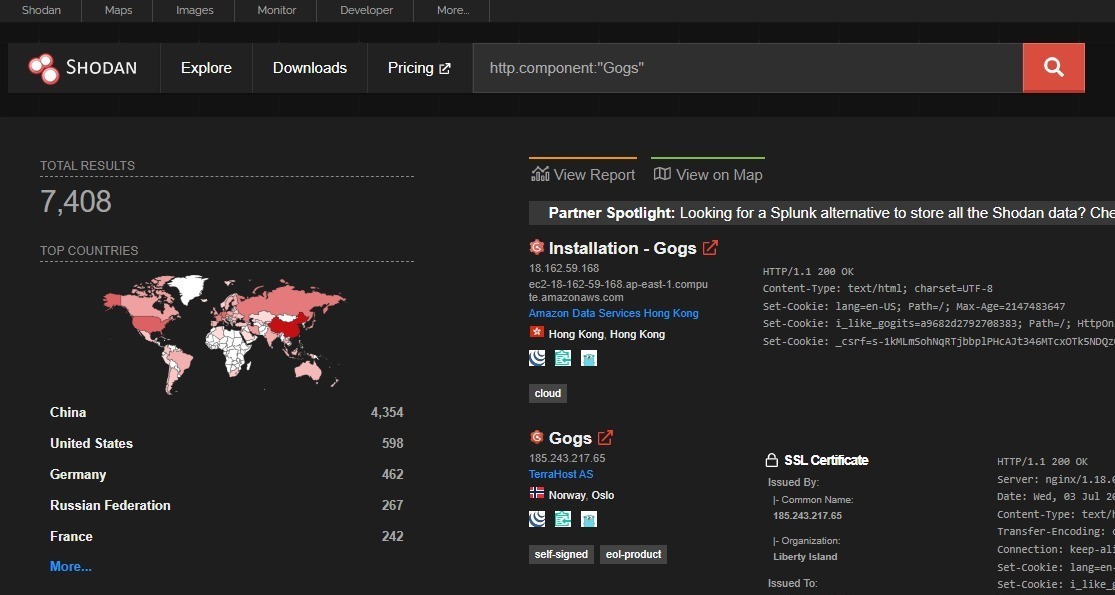
The researchers emphasize that all four vulnerabilities require the attacker to be authenticated, reducing the risk of widespread exploitation but still posing a severe threat to compromised accounts. A Shodan search reveals approximately 7,400 publicly accessible Gogs instances, though the exploitability of these instances remains uncertain.
The argument injection vulnerabilities allow attackers to run commands with the same privileges as the Gogs application, which can lead to unauthorized code access, modification, or deletion. The file deletion vulnerability permits attackers to remove critical internal files.
After initially acknowledging the report in late April 2023, communication from the maintainers dwindled, and no fixes have been implemented until now. The researchers attempted to engage with the maintainers and offered to assist with patches, but these efforts were met with silence.
To mitigate the risks, Chauchefoin and Gerste recommend several immediate actions for Gogs users:
- Disable the built-in SSH server to prevent argument injection attacks.
- Disable user registration to limit potential attackers.
- Apply the patches provided by the researchers, though these are offered without extensive testing.
For long-term security, they advise switching to Gitea, a fork of Gogs that is actively maintained and has already addressed similar vulnerabilities.
Detecting Attacks
Identifying if an instance has been compromised can be challenging. The researchers provide some indicators, such as unusual invocations of the env command with arguments starting with --split-string or HTTP requests targeting specific paths. However, detection methods are not foolproof, and the sophistication of attackers can vary.
