A recent analysis by OVHcloud reveals a new trend in Distributed Denial of Service (DDoS) attacks. The cloud provider’s security team has identified a botnet of compromised MikroTik core routers responsible for high packet rate attacks, which have increased significantly in frequency and intensity since the start of 2023.
DDoS attacks, which aim to disrupt the availability of online services by overwhelming them with traffic, have long been a persistent threat. Traditionally, these attacks involve flooding a target with large amounts of data to exhaust bandwidth or sending numerous application requests to deplete server resources. However, a new method focusing on packet rate rather than bandwidth is emerging, proving to be highly effective and challenging to mitigate.
Packet rate attacks involve sending a high number of small packets to overload the packet processing capabilities of network devices near the target. OVHcloud’s findings indicate that these attacks can cripple critical infrastructure components such as load balancers and anti-DDoS systems, leading to widespread collateral damage.
Increase in high packet rate attacks
According to OVHcloud, a noticeable rise in DDoS attacks exceeding 1 Tbps has occurred since late 2023. While these high-bandwidth attacks were once rare, they have become increasingly common, with attacks reaching 1 Tbps or more occurring almost daily. The most significant attack observed by OVHcloud peaked at 2.5 Tbps.
In parallel, the company has observed a substantial increase in packet rate attacks. Where attacks exceeding 100 Mpps (million packets per second) were once infrequent, OVHcloud now mitigates tens to hundreds of such attacks weekly. In April 2024, the company recorded a record-breaking attack that peaked at 840 Mpps.
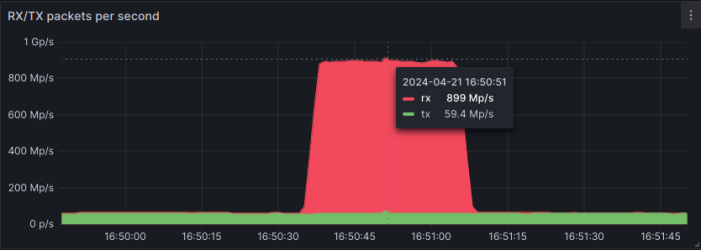
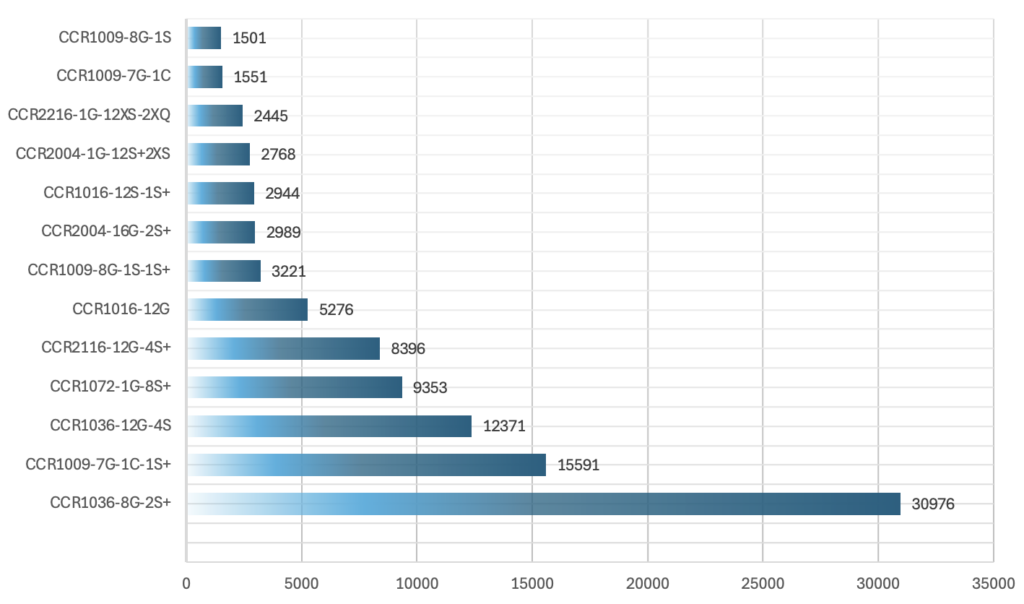
OVHcloud’s investigation into these high packet rate attacks revealed a familiar pattern: many of the attacks originated from a relatively small number of IP addresses, most of which belonged to MikroTik routers. The team identified that these routers, specifically the Cloud Core Router (CCR) models, could generate significant packet rates, with some devices issuing up to 14.8 Mpps each.
Using the cybersecurity search engine Onyphe, OVHcloud found approximately 99,382 MikroTik CCR devices exposed on the internet, with around 40,000 of these identified as capable of generating high packet rates. These devices, designed for core network functions, are not typical residential routers but powerful network hardware meant for high-performance environments.
The investigation also revealed that many compromised MikroTik devices were running outdated versions of RouterOS, MikroTik’s operating system. However, some devices with recent firmware were also implicated, suggesting that the devices might have been compromised before being patched. One potential exploitation method could be the “Bandwidth test” feature in RouterOS, which allows routers to stress-test their throughput capabilities.
Implications and future considerations
The presence of compromised core routers in DDoS botnets poses a significant threat. Due to their strategic network positions and high-capacity connections, these devices can generate and sustain massive attack traffic. This new trend challenges anti-DDoS strategies, which often assume DDoS traffic is dispersed and manageable across global infrastructures.
OVHcloud has already begun adjusting its anti-DDoS infrastructure to cope with these high packet rate attacks. They emphasize the importance of securing network devices and addressing vulnerabilities promptly to prevent such compromises. The company has reached out to MikroTik and relevant Autonomous Systems (AS) to report the issue, but there has been no feedback from MikroTik.
