Popular encrypted messaging app Signal is facing criticism over a security issue in its desktop application. Researchers and app users are raising concerns about how the app handles encryption keys on desktop devices. According to cybersecurity researchers Mysk, the desktop version of Signal stores encryption keys in plain text, an issue that potentially exposes users to data theft.
Mysk detailed the problem on Twitter, highlighting that Signal’s desktop app stores local chat history encryption keys in a plaintext file accessible by any process on the system. “End-to-end encryption is useless if any of the ends gets compromised,” Mysk points out.
According to Mysk, Signal users who link a desktop app may have a false sense of security.
They created a simple Python script that copied Signal’s local storage directory on a Mac, then transferred this data to a fresh macOS installation in a virtual machine. By placing the copied data in the appropriate directory and installing Signal on the virtual machine, they successfully restored their entire Signal session, including chat histories.
The researchers were then able to run three simultaneous active Signal sessions – on the original Mac, an iPhone, and the virtual machine – without any warning from Signal about the cloned session. Messages were delivered to either the Mac or VM, with the iPhone receiving all messages. Importantly, the iPhone still only showed one linked device, failing to detect the unauthorized cloned session on the virtual machine.
The ability to transfer chat histories like this is not limited to macOS. A user on Twitter showed that the encryption keys in Signal’s configuration file on Linux are set with permissions that make them readable by any process the local user runs.
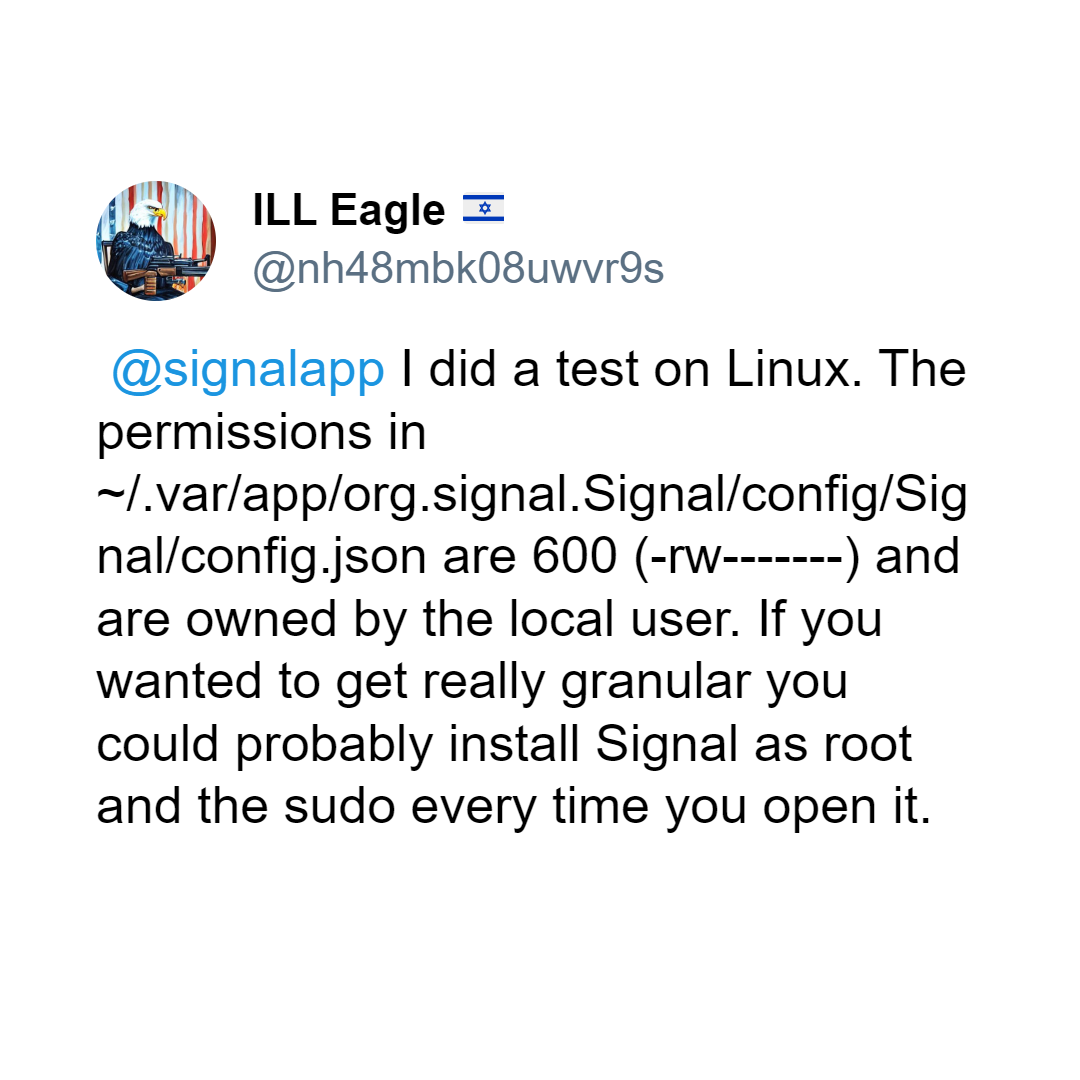
This means that while a keylogger might require admin access to install, any app or script with sufficient permissions could access these plaintext keys.
Naomi Brockwell recommended unlinking any desktop device from Signal accounts. Brockwell explains, “A long-known problem is that Signal stores your decryption key on desktop in a plain text file, NOT your keychain, making it accessible to any app.”
“If you trust your computer, you’re fine,” Brockwell adds, suggesting that users who are cautious about their system’s security might want to reconsider using the desktop version of Signal.
Mysk’s analysis aligns with a 2018 report by BleepingComputer, which also highlighted the poor handling of encryption keys in Signal’s desktop app.
Signal’s approach to end-to-end encryption focuses on protecting data in transit. However, once the data reaches the user’s device, the responsibility for security largely falls on the user. While standard, this practice assumes that users’ devices are secure from malicious software or unauthorized access, which might not always be the case.
In 2018, in response to the BleepingComputer article, Joshua Lund, who works at Signal, said the following,
SQLCipher ships with a good default set of plugins/pragmas, and its performance is excellent because it is built on top of the widely used SQLite database layer. The core premise of the article is completely mistaken. The database key was never intended to be a secret. At-rest encryption is not something that Signal Desktop is currently trying to provide or has ever claimed to provide. Full-disk encryption can be enabled at the OS level on most desktop platforms.
Joshua Lund
Considering this context, it is questionable why Signal stores chat history in encrypted form at all, particularly since media attachments remain unencrypted. It’s clear that Signal has not altered its approach to this issue. We were able to confirm that on a Windows system, Signal continues to store a key in the config.json file in the AppData directory.
On April 1, a pull request was made on GitHub that would alleviate this problem by implementing Electron’s safeStorage API—there has been no follow-up on the request.
Signal response
On July 9, Meredith Whittaker, president of Signal, addressed the concerns raised by the researchers directly on Twitter:
There’s been some chatter about Signal desktop recently, so let’s clear the air. Three points:
- The reported issues rely on an attacker already having full access to your device — either physically, through a malware compromise, or via a malicious application running on the same device. This is not something that Signal, or any other app, can fully protect against. Nor do we ever claim to.
- We continue working to harden our desktop build across supported operating systems and take advantage of new platform capabilities as they emerge. Those of you following our repo can follow this work there.
- The posters who raised this issue did so without contacting us directly. Instead, they went straight to social media, in some cases using inflammatory language. And they dropped these claims over a US holiday weekend. This is the opposite of responsible disclosure.
We ask those who are serious about security and privacy to please engage us directly in the future, instead of resorting first to online claims that can confuse non-experts and lead people to make unsafe choices and develop inaccurate mental models based on scary language. We monitor security@signal.org carefully and respond to all legitimate reports.
The response to Meredith’s statement has varying opinions on social media. Some users argue that the issue of storing encryption keys in plaintext has been known for years, with the initial report dating back to 2018. The idea being that Signal has had ample time to address the problem. Others criticize the assertion that full device access is necessary for exploiting this vulnerability, pointing out that access to user-level files is sufficient.
It’s a tough one to balance. The mixed reactions highlight the tension between immediate security needs and developers’ practical limitations in safeguarding local data. We’ll see if Signal decides to take any steps toward encrypting the key or otherwise making it more difficult for the default user to access the data.
On July 10, one of Signal’s developers finally accepted the safeStorage API pull request on GitHub. We wrote about that here.
Some say this is overblown
Is it possible that the concern about Signal’s desktop encryption key storage may be overblown? One user on Twitter contends that the current setup is “best for the masses, not the extremely security conscious.”
This viewpoint suggests that users highly concerned about potential zero-day exploits or arbitrary code execution should consider more extreme measures, such as setting message expiration timers to very short intervals or avoiding message retention altogether.
The user added, “Even if you install as root and sudo to open it, there are still privilege escalation 0-days, and I’m sure you don’t inspect the source and checksum of all binaries you execute as root. This isn’t as big of an issue as it’s made out to be here.”
Other apps also fall short
The investigation from Mysk was sparked by reports that the ChatGPT MacOS app was storing user conversations without encryption before a recent update. In a post on Mastodon, the researchers noted that this practice is common among many applications.
They cited WhatsApp and Apple’s iMessage as examples. WhatsApp’s chat content can be accessed by any other launched application without restriction. iMessage, however, stores data in a sandbox, preventing unauthorized processes from accessing it.
In both cases, attackers must first gain access to the local user account to reach such application data. Once this access is obtained, other data is typically also vulnerable, including locally stored documents that are usually unencrypted unless users take specific measures.
The researchers point out that the level of protection needed for chat content compared to other locally stored data may vary depending on the specific situation.
This article was updated on July 9, 2024, at 15:50 GMT to include a response from Signal. On July 12, 2024, at 8:38 GMT this article was updated once more to include mention of Signal going forward with the safeStorage API solution.
