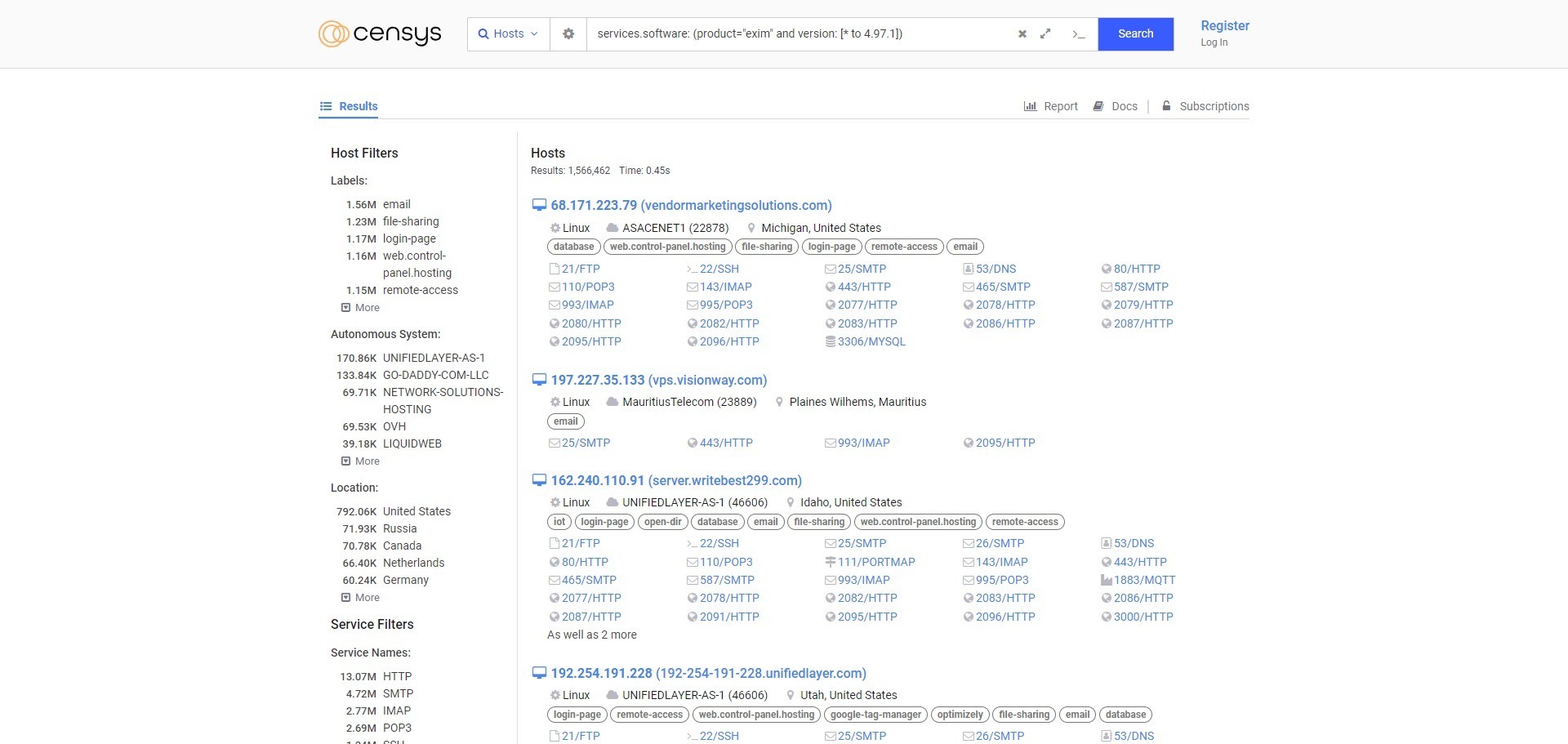
A critical security vulnerability in the widely-used mail transfer agent (MTA) Exim has put over 1.5 million email servers at risk worldwide. This issue, identified as CVE-2024-39929, allows attackers to bypass Exim’s protection mechanism and deliver executable email attachments unfiltered to end users’ mailboxes. According to security experts at Censys, all Exim versions up to and including 4.97.1 are affected.
Exim is a highly popular MTA, especially on Unix-like operating systems, handling a substantial portion of email traffic globally. According to the Censys report, 74% of the 6.5 million SMTP mail servers are accessible via the Internet using Exim, equivalent to approximately 4.83 million servers. Of these, 1,567,109 are running vulnerable versions, including over 790,000 in the United States alone.
The vulnerability stems from an error in parsing RFC-2231 headers, which manage how file names in email attachments are encoded and interpreted. When exploited, this flaw can allow malicious attachments to bypass security filters that block specific file types, such as executables, from reaching users’ inboxes.
While no active exploitation cases have been reported, a proof of concept is available, suggesting that attackers could soon leverage this vulnerability. Censys has classified this CVE as critical, with a CVSS score of 9.1, indicating a high potential impact if exploited.
A patch for this vulnerability is available through the release of Exim 4.98. This version includes fixes not only for CVE-2024-39929 but also introduces several new features and improvements. Among these updates are enhancements to the DKIM (DomainKeys Identified Mail) mechanism, the ability to limit the number of recipients per message, and additional support for internal databases, including SQLite3.
This is not the first time Exim has faced critical security vulnerabilities. In September 2023, a different severe flaw reported by the Zero Day Initiative (ZDI) affected millions of Exim servers. However, a patch was delayed due to communication issues between the ZDI and Exim developers, exposing many systems for a prolonged period.
