The Chrome Security Team has announced a change that will impact many websites starting in late 2024. This change concerns the digital certificates that secure websites and ensure your connection to them is safe.
Digital certificates (SSL/TLS) prove that the site you’re visiting is the real deal and not an imposter trying to steal your information. These certificates are issued by organizations called Certification Authorities (CAs). Chrome relies on a list of trusted CAs to ensure these certificates are legitimate.
However, Chrome plans to remove some Entrust certificates from its list of trusted certificates starting in version 127. The reason? Entrust has been scrutinized for mistakes and issues over the past few years. The Chrome team mentioned, “Over the past six years, we have observed a pattern of compliance failures, unmet improvement commitments, and the absence of tangible, measurable progress.” In simpler terms, Entrust has repeatedly failed to meet the high standards required to be a trusted CA.
Google has also stated that this change will affect AffirmTrust, a lesser-known certificate provider that, in its own words, provides “Low-cost SSL/TLS that doesn’t skimp on security.” However, given the news today, that doesn’t seem the case.
Although Entrust (0.1%) is not nearly as popular as Let’s Encrypt (49.7%) or IdenTrust (15.6%), sites using Entrust certificates include ESPN, IRS.GOV, NIH.GOV, Bank of America, and others.
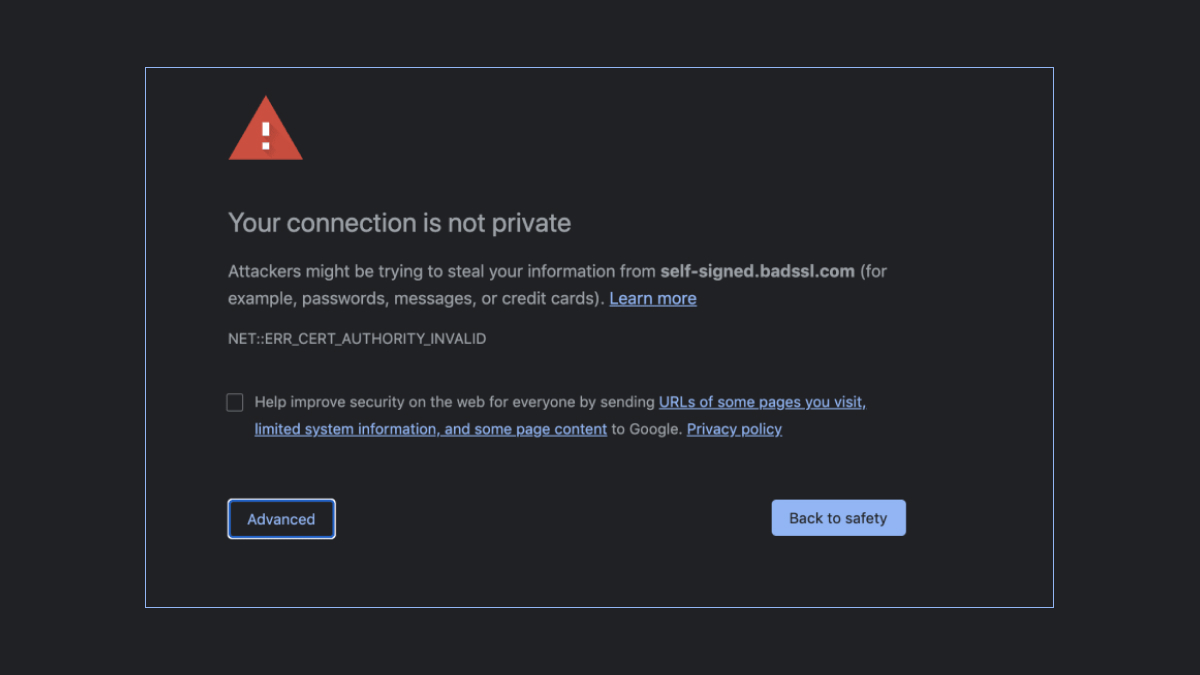
So, what does this mean for users? Starting November 1, 2024, if a website uses one of the Entrust certificates that Chrome no longer trusts, you will see a warning message instead of the website. This warning will look like a full-page alert, telling you the site is not secure.
This change is specifically for certificates issued after October 31, 2024. In other words, this will not affect websites with their Entrust certificate issued before this date. However, certificates naturally expire, and you will need to find a new Certificate Authority.
But why is Chrome doing this? The internet’s security relies on trust. When a CA fails to maintain the required standards, it poses a risk to everyone who uses the internet. Chrome’s team stated, “It is our opinion that Chrome’s continued trust in Entrust is no longer justified.” Chrome aims to protect users from security threats by removing trust in these certificates.
This means website owners need to take action. If they are using an Entrust certificate that will be affected by this change, they need to switch to a different CA before their current certificate expires: we recommend Let’s Encrypt, which is free. This might sound like a hassle, but it’s necessary to ensure visitors can access your websites without issues.
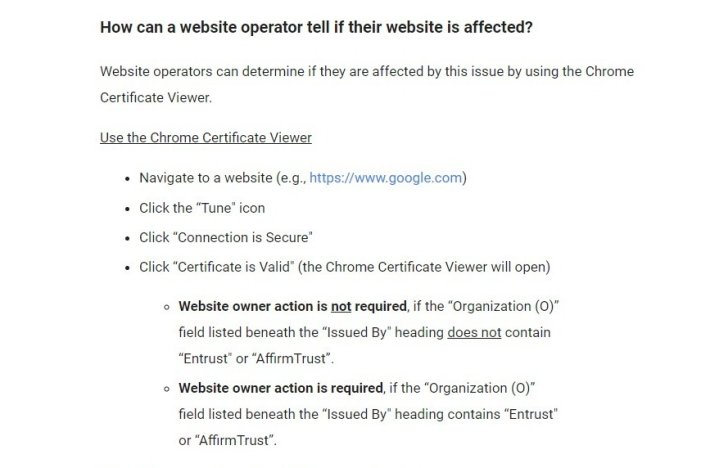
The blog post says users can use the Chrome Certificate Viewer to see if Entrust issued their certificate. If it did, they must quickly switch to a new CA.
There are some good news for those running internal networks in large organizations: Chrome allows enterprises to override these changes by installing the affected certificates as trusted on their local networks. This means internal websites can continue to function without disruption, even if they use the impacted Entrust/AffirmTrust certificates.
Additional context from Bugzilla
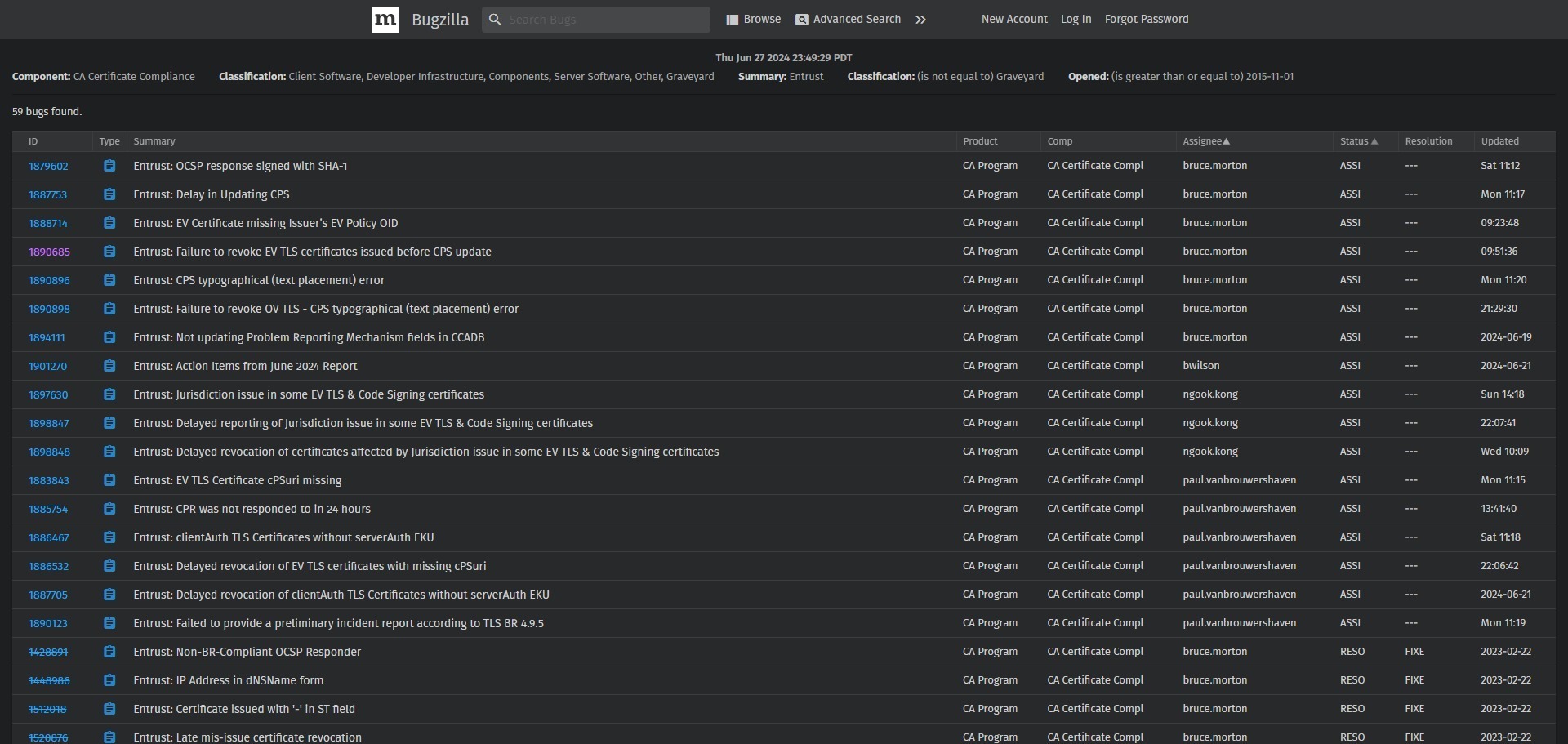
A discussion on Mozilla’s Bug Tracker (Bugzilla) tracked under Bug 1890685 reveals that Entrust failed to revoke some Extended Validation (EV) TLS certificates, a severe compliance issue. These certificates, issued between March 18 and March 21, 2024, did not follow the Certification Practice Statement (CPS) published at that time.
Entrust decided not to revoke these certificates, arguing that doing so would confuse their customers and claiming there was no security risk. However, this decision sparked criticism. Commenters on Bugzilla emphasized that failing to follow revocation procedures increases uncertainty around Entrust’s trustworthiness. They also pointed out that the failure to revoke these certificates was seen as a pattern of prioritizing customer convenience over strict adherence to security rules.
One commenter noted, “The pattern I’m seeing is: putting customers ahead of Public WebTrust rules, not responding to actual incidents until root programs start asking questions, and rushing responses to incidents without proper data backing.”
In a detailed post on Google Groups, Mike Shaver highlighted concerns with Entrust’s ability to adhere to WebPKI and Mozilla Root Store Program (MRSP) requirements. Despite updated reports and responses, Entrust’s handling of certificate revocation, operational accountability, and transparency remain problematic.
Shaver criticizes Entrust’s tendency to prioritize customer convenience over strict compliance, insufficiently detailed organizational changes, and failure to meet Mozilla’s incident response requirements. He concludes that without concrete improvements and transparency, continued trust in Entrust-issued certificates poses substantial risks to the web PKI and Mozilla’s users.
At the time of publishing this article, Entrust had not made a public comment on the changes that Google will impose on them.
