A new malvertising campaign targeting Mac users has been uncovered, using fake advertisements for the up-and-coming Arc web browser to distribute malware. According to cybersecurity researchers at Malwarebytes, the campaign, observed on June 24, 2024, is deploying a sophisticated infostealer dubbed “Poseidon.”
The researchers found that cybercriminals are exploiting Google’s advertising platform to place malicious ads that appear when users search for the Arc browser. Clicking on these ads redirects victims to a convincing but fraudulent website mimicking Arc’s official page.
Jérôme Segura, a researcher at Malwarebytes, noted that this is the second instance in recent months where Arc has been used as bait in malvertising schemes. “It’s certainly a sign of Arc’s growing popularity,” Segura commented.
The Poseidon malware, previously tracked as OSX.RodStealer, is reportedly being developed as a competitor to the notorious Atomic Stealer. Researchers found that a significant portion of Poseidon’s code base is similar to its predecessor, with added features such as the ability to extract VPN configurations.

According to the report, the malware’s creator, known by the handle “Rodrigo4” in underground forums, has been actively promoting Poseidon as a “malware-as-a-service” offering. The package includes a control panel with statistics and a customizable builder, allowing criminals to tailor the malware’s appearance and behavior.
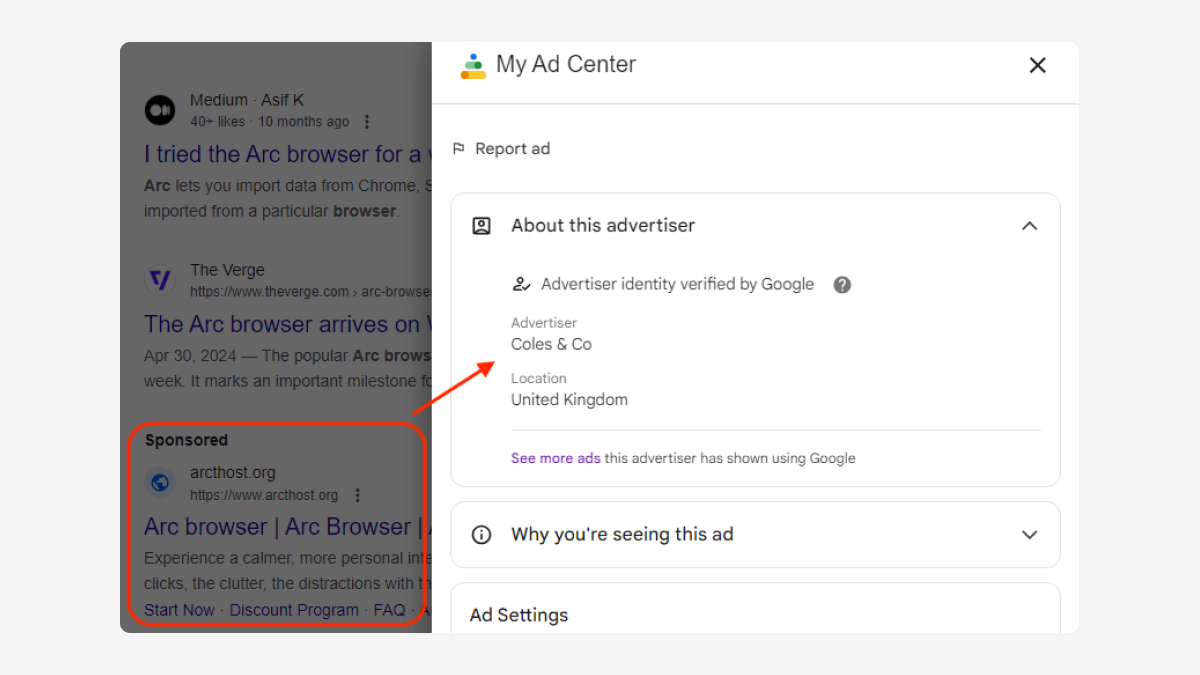
The researchers discovered that the malvertising campaign used a fake company name, “Coles & Co,” to place the deceptive Google ads. Users who clicked on these ads were directed to a domain called arc-download[.]com, which hosted a malicious disk image file designed to bypass Mac security measures.
Malwarebytes emphasized the growing threat of Mac-focused malware, particularly infostealers. They warned that the repeated occurrence of such campaigns confirms these threats’ real and active nature.
These malvertising cases often go undetected by Google’s automated systems. The company typically addresses such issues only after receiving specific reports from users or security researchers. In this instance, Malwarebytes confirmed they had shared information about the malicious Arc browser ad with Google. However, this reactive approach means that many users may be exposed to threats before they are removed.
To protect against such attacks, we recommend using web protection tools that block ads and malicious websites. You should also always remain mindful when downloading and installing new applications, even from seemingly legitimate sources.