The widely-used RADIUS protocol, essential for network access control, is now threatened by a new vulnerability called “Blast-RADIUS.” This security flaw, identified by researchers from several universities, Microsoft, and the Dutch Centrum Wiskunde & Informatica (CWI), allows attackers to bypass authentication mechanisms and gain unauthorized access to network devices.
Vulnerability Details
RADIUS, or Remote Authentication Dial-In User Service, has been a cornerstone of network security since its inception in 1991. It is used extensively for authenticating and authorizing access to Wi-Fi and VPN networks, as well as other network devices like routers and switches. Typically, RADIUS traffic is transmitted insecurely over the UDP network layer and relies on the outdated MD5 cryptographic hash function for security. MD5 has been known to be vulnerable since 2004, yet the RADIUS protocol has seen little modification to address these concerns.
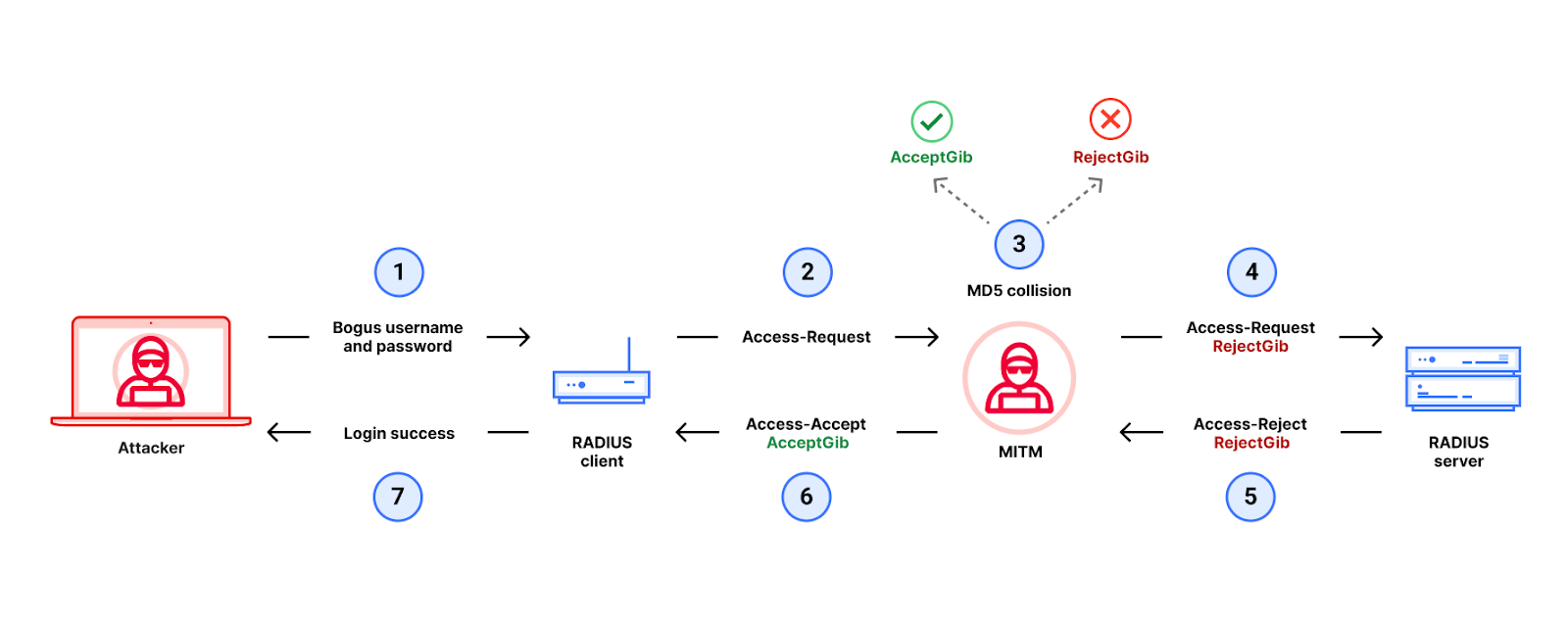
According to the researchers, the Blast-RADIUS attack leverages a man-in-the-middle position to forge valid “accept messages” in response to failed authentication attempts. This allows attackers to access network devices without needing to crack passwords or shared secrets. Crucially, the attack does not expose the user’s credentials to the attacker.
“Our attack combines a novel protocol vulnerability with an MD5 chosen-prefix collision attack and several performance improvements,” the researchers explained. This new method significantly reduces the time needed to exploit MD5 vulnerabilities, enabling the attack to be carried out within minutes instead of days.
Implications and Affected Systems
The vulnerability impacts all RADIUS implementations using non-EAP authentication methods over UDP. This includes a wide range of applications, from enterprise networks to ISP services, and even mobile networks. Notably, the attack requires an attacker to have man-in-the-middle access, meaning they must be able to intercept and manipulate traffic between the RADIUS client and server.
Marc Stevens of CWI emphasizes the urgency of the issue: “The use of MD5 has long been discouraged, but often, concrete attacks are needed to spur action. The RADIUS/UDP standard has failed to meet modern cryptographic standards for too long. We recommend transitioning to RADIUS/TLS, which provides stronger security guarantees.”
Mitigation and Recommendations
Administrators are urged to check for patches and implement immediate mitigations. The short-term solution requires that clients and servers always use Message-Authenticator attributes in all requests and responses. This helps prevent the Blast-RADIUS attack by adding a layer of verification that cannot be easily forged.
For long-term security, the transition to RADIUS/TLS is advised. TLS, or Transport Layer Security, provides encryption and authentication that meet modern standards, fitting well within zero-trust architectures where no part of the network is inherently trusted.
Cloudflare and the CERT Coordination Center (CERT/CC) at Carnegie Mellon University have published vulnerability analyses (here and here, respectively), highlighting its severity and the need for swift action. Alan DeKok of FreeRADIUS detailed the attack methodology and mitigation strategies in a white paper, and further insights will be presented at the upcoming USENIX Security Symposium in August.
Conclusion
The Blast-RADIUS attack highlights the pitfalls of clinging to outdated cryptographic methods. With network security threats continually evolving, the protocols designed to protect our systems must keep pace. Administrators must swiftly patch these vulnerabilities and transition to more secure standards like RADIUS/TLS to shield their networks from this and future attacks.
This incident is a wake-up call about the dangers of complacency in security practices. As Stevens aptly says, “We cannot afford to wait for attacks to happen before taking action.” We’re practically inviting them if we don’t stay ahead of these threats.
