In a freshly published report titled “Caught in the Net,”, Recorded Future’s Insikt Group reveals the potential of infostealer malware data to identify and track consumers of child sexual abuse material (CSAM). This report leverages Recorded Future’s Identity Intelligence to unearth 3,300 unique individuals engaged in CSAM activities, surfacing new sources and uncovering geographic and behavioral trends.
The study highlights that infostealer logs can be instrumental in identifying CSAM consumers and trends within these illicit communities. Insikt Group’s investigation identified approximately 3,300 users with accounts on at least one CSAM source, with about 4.2% having credentials for multiple sources. This multiplicity of accounts may indicate a higher likelihood of criminal behavior against children, according to the report.
Using a combination of infostealer data and open-source intelligence (OSINT), Insikt Group conducted detailed investigations on three individuals, identifying two and uncovering digital artifacts, including cryptocurrency addresses, for a third.
Infostealer malware, often spread through phishing campaigns, fake update websites, and malvertising, is capable of stealing a wide range of sensitive information. This includes account login credentials, cryptocurrency wallets, payment card data, and more. Threat actors can use this stolen data to gain unauthorized access to networks or monetize it by selling it on dark web sources.
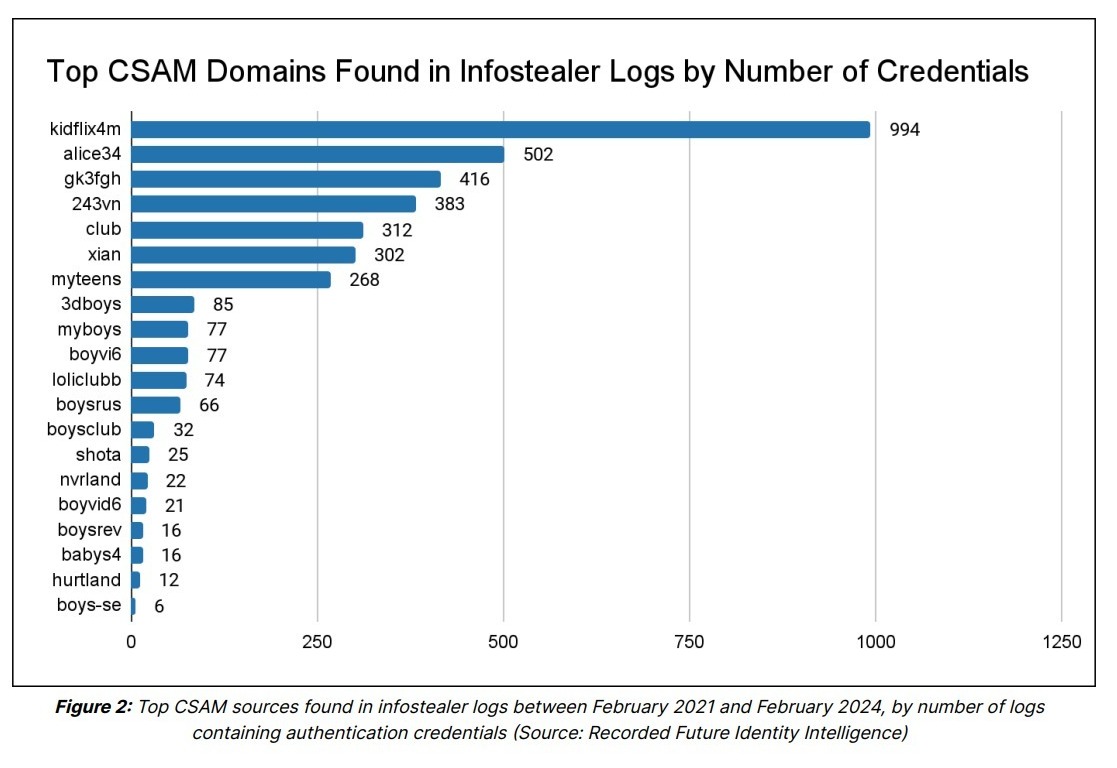
Recorded Future’s Identity Intelligence, a dataset of 25 billion credentials with an ingestion rate of 150 million per month, was queried to identify users with login credentials to known CSAM domains. This analysis revealed 3,324 unique credentials used to access CSAM websites between February 2021 and February 2024.
The report reveals that Brazil, India, and the United States dominate the user counts accessing CSAM communities. This is attributed to higher rates of infostealer infections in these countries, potentially due to widespread software piracy in Brazil and large populations in India and the US.
Normalizing the data to account for potential biases, Eastern European countries such as Ukraine and the Czech Republic also emerge as significant sources.
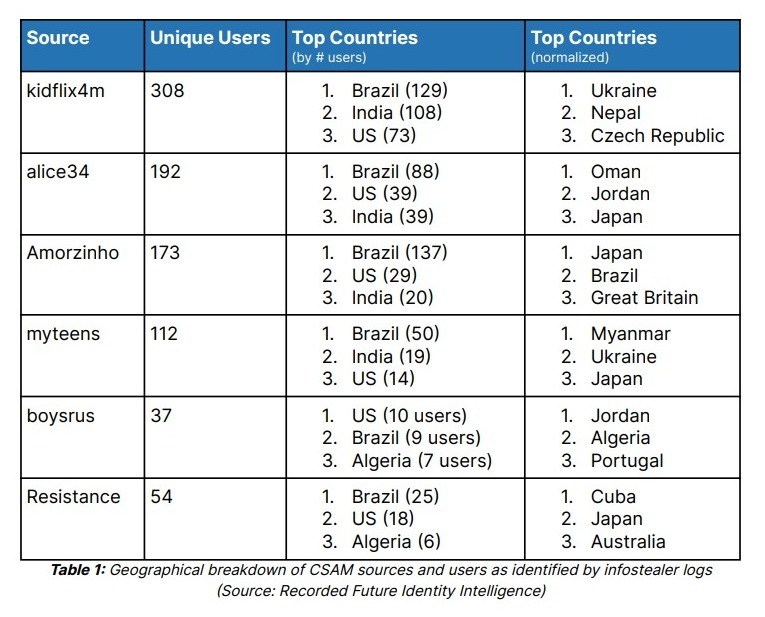
The investigation identified 141 “repeat offenders” with accounts on multiple CSAM sources, including ten cryptocurrency wallet addresses.
The report details three case studies:
- “d“: A Previous Offender – This user, identified through infostealer logs, had accounts on multiple CSAM websites and a history of child exploitation convictions. The investigation connected them to clear web services and personal details, revealing a troubling pattern of behavior.
- “docto”: An Unreported Abuser – This individual, active on nine CSAM websites, had no prior convictions but sought volunteer and employment opportunities involving children. Their extensive online footprint included clear web accounts and Google searches related to children’s hospitals.
- “Bertty”: A Cryptocurrency User – Linked to active cryptocurrency wallets with historical transactions, this user’s activities suggest involvement in the purchase and production of CSAM material. The presence of the MEGA file-sharing service on their device, known for its association with CSAM content, adds to the suspicion.
The study demonstrates how this type of data analysis could potentially uncover previously undetected child exploitation activities. In one case study, the researchers claim they identified an individual with access to multiple CSAM websites who appeared to be seeking opportunities to work with children, despite having no prior criminal record.
In closing remarks, the researchers said they believe their methodology could help track the lifecycle of CSAM websites, identify new platforms as they emerge, and potentially assist in prosecution efforts. However, they emphasize that their dataset is limited and further research would be needed to draw broader conclusions.
As infostealer attacks continue to proliferate, the report suggests that analyzing stolen data may provide an increasingly valuable source of intelligence for cybersecurity professionals and law enforcement working to combat online child exploitation.
You can view the full research paper (pdf) on Recorded Future’s website!
