The Chrome Web Store is a platform where users can find and install extensions to enhance their browsing experience on Google Chrome. These extensions range from productivity tools to entertainment applications, catering to over 1.6 billion active users. However, this immense popularity comes with a downside: extensions often have access to sensitive information and can introduce security vulnerabilities.
Researchers from Stanford University and CISPA Helmholtz Center for Information Security have investigated the Chrome Web Store, uncovering a landscape riddled with potential security hazards.
Their study, “What is in the Chrome Web Store? Investigating Security-Noteworthy Browser Extensions,” published in June 2024, provides a comprehensive look at the extension ecosystem and raises alarming questions about the safety of the tools many use daily to enhance our browsing experience.
The methodology
To investigate the Chrome Web Store (CWS), the researchers utilized historical data from ChromeStats, which archives browser extension information. They collected data on extensions available between July 2020 and February 2023, including metadata and, where possible, source code. The extensions were categorized into two main groups: likely-benign and security-noteworthy extensions (SNE), which included malware-containing, policy-violating, and vulnerable extensions. They used the ChromeStats API to download and unpack extensions’ source codes, then employed ssdeep fuzzy hashing to identify clusters of similar extensions. They traced the origins of code reuse by extracting URLs from comments in the code. The team also analyzed the extensions’ lifecycles, update histories, user counts, developer patterns, permissions, and the prevalence of vulnerable libraries using tools like RetireJS.
The findings and results
The study starts by highlighting the surprisingly short lifespan of many extensions. The researchers found that only about 60% of extensions remain in the store after one year. On average, 3,775 extensions are removed, and 2,687 are added to the CWS monthly, indicating significant volatility. Only 51.86–62.98% of extensions added in 2021 were available after one year. Extensions with larger user bases tend to remain longer.
However, the real red flag is what the researchers call “Security-Noteworthy Extensions” or SNE. These include extensions containing malware, those violating Chrome Web Store policies, and those with known vulnerabilities.
Over 346 million users installed at least one SNE in the past three years (2020 -> 2023):
- Malware-containing extensions: 280 million users.
- Policy-violating extensions: 63 million users.
- Vulnerable extensions: 3 million users.
They found that these security-noteworthy extensions often linger in the store for years. The average malware-containing extension, for instance, stays available for 380 days before being removed. Vulnerable extensions fare even worse, remaining in the store for an average of 1,248 days – that’s nearly three and a half years of potential exposure for users.
Their research showed that 31.5% of extensions rely on at least one vulnerable JavaScript library, impacting nearly 500 million users.
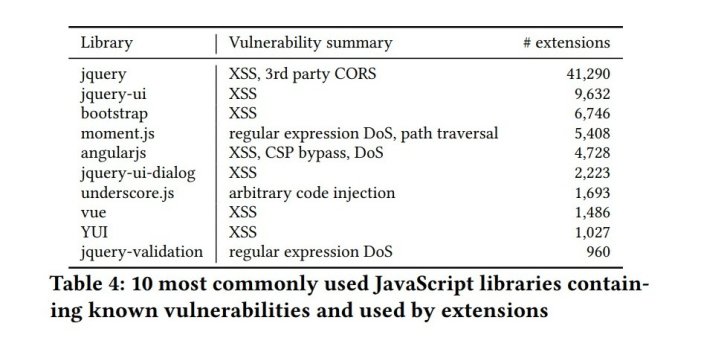
The researchers also uncovered interesting patterns in the code of extensions. They found extensions frequently share code bases, often from public repositories or forums, leading to clusters of similar extensions.
While some of these are likely benign – different versions of the same extension, for example – others raise red flags. For instance, 816 new extensions used the outdated Extensionizr project (last updated 7 years ago), leading to the use of vulnerable libraries.
Out of 108,859 extensions analyzed, 20,822 contained similar scripts, forming 3,270 clusters. 321 clusters contained only SNE, suggesting that code similarity can help flag suspicious extensions.
Their research also revealed that many extensions are never updated after they’re first released—in fact, 60% have never been updated at all! This lack of updates can be a big problem because any security issues in the extension will never get fixed.
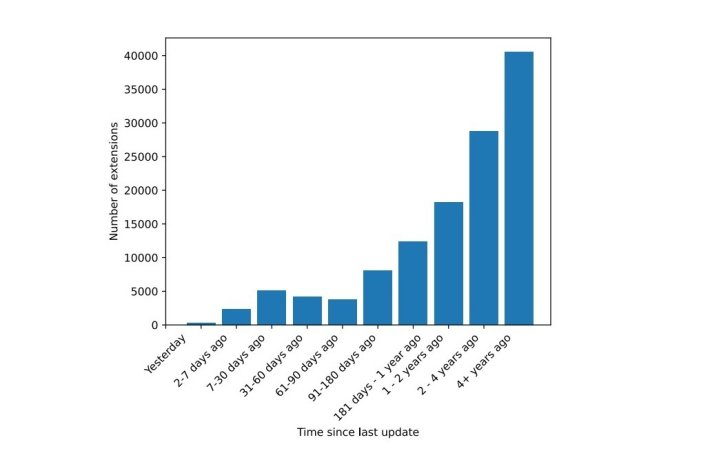
The researchers also found that half of the known vulnerable extensions stayed that way for at least two years after discovering their issues. This lack of maintenance leaves extensions vulnerable to newly discovered security flaws and unable to adapt to browser or web standards changes.
One of those changes is the adoption of Manifest V3, Google’s new extension framework designed to improve security. Despite its benefits (but also downsides), as of February 2023, 74% of extensions still used the older, less secure Manifest V2.
It’s worth pointing out that on May 30, 2024, Google officially announced that the phase-out of Manifest V2 had begun.
Starting on June 3 on the Chrome Beta, Dev and Canary channels, if users still have Manifest V2 extensions installed, some will start to see a warning banner when visiting their extension management page – chrome://extensions – informing them that some (Manifest V2) extensions they have installed will soon no longer be supported. At the same time, extensions with the Featured badge that are still using Manifest V2 will lose their badge.
Google
Google also said that in the coming months, those extensions will gradually be disabled. Users will be directed to the Chrome Web Store, where they will be recommended Manifest V3 alternatives for their disabled extensions. For a short time after the extensions are disabled, users will still be able to turn their Manifest V2 extensions back on, but over time, this toggle will also be removed.
Recommendations
The researchers suggest several recommendations to enhance the safety of browser extensions:
- Given the high turnover of extensions, regular studies are essential to ensure that research reflects the current state of the CWS. Longitudinal studies provide the best assurance of temporal representativeness.
- Google should implement better detection mechanisms for SNE. This includes flagging extensions with similar code bases or those from developers with a history of publishing SNE.
- Users should be notified about the risks of SNE and unmaintained extensions. Improving user awareness can help them make more informed decisions when installing extensions.
For developers, the message is clear: regular maintenance is crucial. This includes updating the extension’s core functionality, keeping any included libraries up to date, and transitioning to more secure frameworks like Manifest V3 when possible.
As users, we should be more cautious about the extensions we install and perhaps regularly review the extensions we have installed, removing those that are no longer actively maintained. There are good reasons for this also.
Back in 2021, the maintainer of the Chrome extension “Hover Zoom+” (300,000 users) published a GitHub Issue titled “Temptations of an open-source browser extension developer.” In it, he showed how malicious actors had asked him to install malicious tracking codes in his extension, or flat-out offered him money to purchase the extension altogether, which could then be exploited for personal gain.
Not everyone has a high moral compass and can refuse $10,000 or even $50,000 for their extension, even if they know that the new owner will exploit its users.
Having actual studies that reveal the potential attack vectors of what we all actively add to our web browsers goes a long way.
