Despite Internet Explorer (IE) being officially retired and disabled in modern Windows systems, attackers have found ways to exploit its remnants to target users. Microsoft, which ended support for IE on June 15, 2022, and disabled it in Windows 10 and 11, released security updates earlier this month to address this vulnerability. Trend Micro’s Zero Day Initiative first reported the issue and has since been elaborated upon by both Trend Micro and Check Point Research.
Trend Micro’s Zero Day Initiative discovered that attackers could exploit a vulnerability in the MSHTML platform of Windows, which allows HTML Application (HTA) files to be launched via the disabled IE process. Although IE is no longer accessible to average users—attempting to open IE redirects to Microsoft Edge—its components still exist within the system. This hidden presence creates an attack vector.
According to Trend Micro, “even though users can no longer access IE, attackers can still abuse Windows leftovers on their machines, such as IE, to infect users and organizations with ransomware and backdoors, or use it as a proxy to execute other malware.”
Attack Mechanism
The attackers distributed malicious files using zip files disguised as ebooks in PDF format. These files, named with a “.pdf.url” extension, tricked users because Windows does not show file extensions by default. When users opened these files, an HTA file was downloaded, prompting them to open or save it.
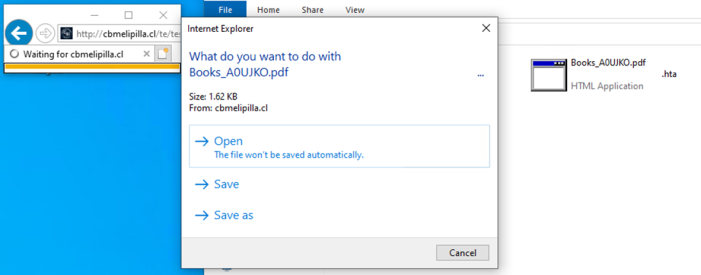
Opening the HTA file executed info stealer malware that collected passwords, cookies, and other data, sending it back to the attackers. The malware also allowed for the installation of additional malicious software.
CVE-2024-38112
This particular vulnerability, identified as CVE-2024-38112, was used by the advanced persistent threat (APT) group Void Banshee. The group exploited this zero-day vulnerability to access and execute files through the disabled IE, using MSHTML and internet shortcuts (URL files). Void Banshee’s campaign primarily targeted North America, Europe, and Southeast Asia, spreading malware that steals sensitive data from various applications.
“Even though IE is no longer active, its large attack surface and the lack of updates make it a serious security problem for Windows users,” Trend Micro concluded.
In response to the discovery, Microsoft unregistered the MHTML handler from Internet Explorer in the July 2024 Patch Tuesday update. This change prevents MHTML from being used within internet shortcut files, thereby closing the exploited vulnerability.
Trend Micro and Check Point Research recommend regularly updating all software to protect against such vulnerabilities. Users should also be cautious when opening files with suspicious extensions and enable the display of file extensions to avoid being tricked by disguised malicious files.
