So, you’re on the hunt for top-grade file encryption software? In a world where data breaches are more than just headline material, safeguarding your sensitive information isn’t optional; it’s a necessity. In this article, we cut through the noise to present you with reliable encryption tools that won’t let you down.
We’ll dissect features, ease of use, and levels of security—without skimping on the details. Whether you’re looking to protect personal files or fortify business data, we’ve got you covered. After all, why settle for subpar when you can have the best? Keep reading to find your ideal shield against unauthorized access.
How does file encryption software work?
File encryption software operates on a straightforward yet robust principle: it transforms readable files (plaintext) into an unreadable format (ciphertext) using a specific algorithm and an encryption key.
Only those with the corresponding decryption key can reverse this transformation and access the original data. Essentially, it’s like putting your data in a vault that only you—or someone you trust—can open.
There are different types of encryption algorithms—AES (Advanced Encryption Standard), RSA, and Triple DES, to name a few. Each has its own way of shuffling the bits and bytes, but the objective remains the same: make the data unreadable to anyone who isn’t supposed to see it.
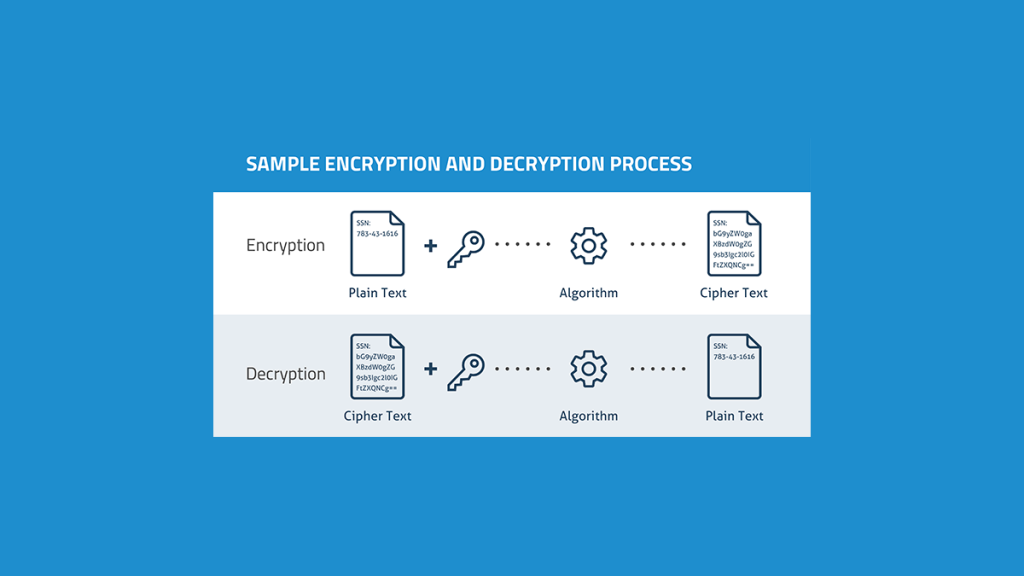
Now, you might be thinking, what about the encryption key? Well, it’s either a series of random characters or, in more advanced setups, a cryptographic key generated by the software itself. If you’re using symmetric encryption, the same key is used for both encryption and decryption. In asymmetric encryption, a pair of keys is used: one for encryption and another for decryption. The public key is open for anyone to use to encrypt a message, but only the private key can decrypt it.
So why do you need encryption software specifically? Because manually encrypting each file is not only cumbersome but also prone to errors. Good encryption software automates the process, ensures it’s done correctly, and often comes with extra features like secure file deletion, password management, and multi-device support.
To sum up, file encryption software serves as a reliable gatekeeper for your data, ensuring that your files remain impenetrable to unauthorized access. And in a time when data is as precious as gold, having a virtual Fort Knox certainly won’t hurt.
VeraCrypt
VeraCrypt is an open-source disk encryption software that’s been around since 2013. Developed as a successor to TrueCrypt, which was discontinued, it provides robust encryption features for safeguarding your data. VeraCrypt uses powerful encryption algorithms like AES, TwoFish, and Serpent, making it a strong choice for anyone concerned about data privacy.
So why should you care about VeraCrypt? Imagine you’ve got a folder on your computer labeled “Personal.” Inside, you’ve got tax records, private photos, and perhaps even a diary. If your computer were to be stolen or hacked, all that information would be easily accessible.
With VeraCrypt, you can turn that folder into a secure vault that’s locked behind complex mathematics. Even if someone gains access to your machine, cracking open this vault would be an extremely difficult task, to say the least.
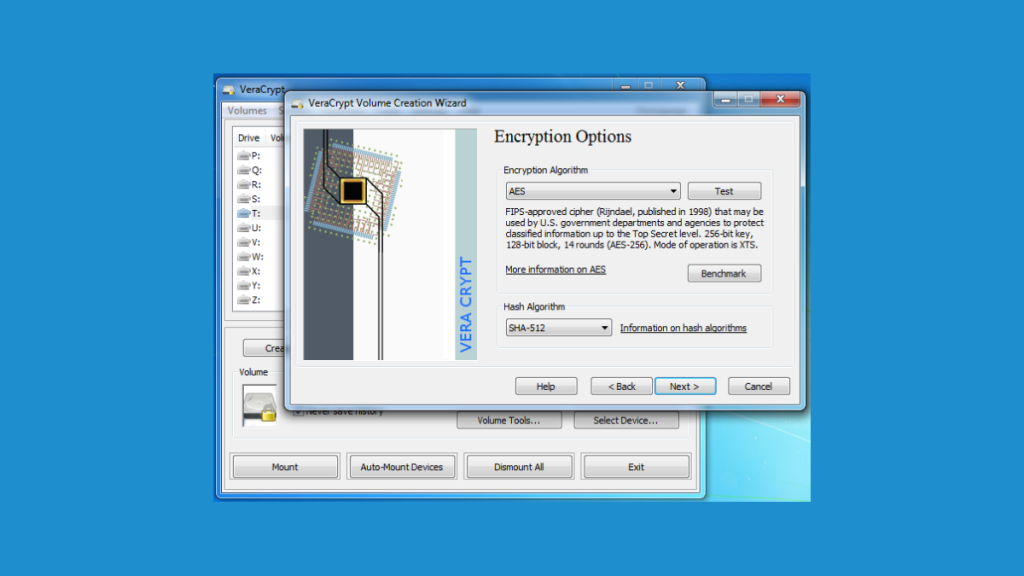
Getting started with VeraCrypt is straightforward. You download the software, run the installation process, and then open the application. From there, you can either encrypt an entire disk, like a USB drive, or create a virtual encrypted disk, which would be a file that acts like a real disk when mounted. The process is fairly intuitive, guided by wizards that walk you through each step. Once set up, accessing your encrypted files is as simple as unlocking the virtual disk with your password, which then mounts it as a regular drive on your computer.
But is VeraCrypt for everyone? Not necessarily. If you’re only looking to encrypt a few files or folders, the software might seem like overkill. Moreover, forgetting your password could mean losing access to your files for good, as there’s no ‘Forgot Password’ option with this level of security.
So, should you use VeraCrypt? If you have sensitive files that you absolutely cannot afford to be compromised, then yes. It offers a level of security that’s hard to beat. But remember, with great power comes great responsibility—in this case, the responsibility to remember your password and to understand that you’re using a powerful tool designed for robust security.
GNU Privacy Guard
GNU Privacy Guard, commonly known as GnuPG or GPG, is an open-source encryption software that’s designed to secure your data. At its core, GnuPG uses a method of encryption called public-key cryptography. Imagine you have a secure mailbox only you can open; that’s what GnuPG aims to give you in the digital realm. The “keys” in this case are a set of long numbers and letters. You get two keys: one public that you share with others, and one private that you keep to yourself.
So, what’s the real-world utility of GnuPG? Let’s say you need to send confidential information, like your financial records, to your accountant. Normally, you’d be hesitant to send such sensitive data via email. With GnuPG, you can encrypt the file using your accountant’s public key. Once encrypted, only your accountant, who has the corresponding private key, can decrypt and read the file.
Another scenario involves verifying the authenticity of a document. If you’ve ever received an email and wondered, “Did this really come from my bank?”, GnuPG offers a way to be certain. You can use it to create a digital signature that serves as a digital fingerprint, confirming that a message or document is genuinely from the person who claims to have sent it.
GnuPG isn’t just for email or document encryption. Software developers often use it to sign code packages, confirming that the code hasn’t been tampered with. Journalists might use it to protect a sensitive source. Even on a personal level, if you’re storing important files on a cloud service, you can use GnuPG to encrypt them before uploading, adding an extra layer of security.
In summary, GnuPG is a versatile tool for encrypting data and authenticating messages. It gives you the power to secure your communications and files, so you can navigate the complexities of the digital world with a bit more peace of mind.
7-Zip
7-Zip is a popular, open-source file archiver with a strong focus on security. Developed by Igor Pavlov, the tool has become a go-to for users who need to compress or decompress files. It supports a multitude of archive formats including its native 7z, as well as ZIP, TAR, and even RAR. But what sets 7-Zip apart? It’s the software’s encryption capabilities.
When you need to send sensitive documents via email or keep your personal data away from prying eyes, 7-Zip has you covered. It uses AES-256 encryption, an industry-standard algorithm that has yet to be cracked. Encrypting your files is straightforward; simply add the files to a new archive and set a password. And voila, your data is now tucked away in an encrypted archive.
Use Cases
- Secure Email Attachments: Sending a confidential contract to a client? Use 7-Zip to create an encrypted archive, then email the 7z or ZIP file. The recipient can easily open it using the password you provide.
- Cloud Storage: Sure, your Dropbox account has a password, but what about an extra layer of security? Before uploading, wrap your files in a 7-Zip encrypted archive.
- Local Storage: Your laptop could be stolen or hacked. Storing sensitive files like tax documents? Encrypt them with 7-Zip before saving them on your disk.
- File Sharing: Passing around a flash drive at a meeting? Use 7-Zip to ensure that only intended recipients can access the files.
So, why opt for 7-Zip over other encryption methods? For one, it’s free. Second, it’s open-source, meaning that its source code has been scrutinized by security experts across the globe. And third, it’s user-friendly—no need for a manual or tech support.
To sum it up, 7-Zip isn’t just a tool for compressing files; it’s a versatile utility for safeguarding your digital life. Easy to use and secure, it’s an excellent choice for those looking to keep their data under wraps.
Cryptomator
Cryptomator is a client-side encryption software designed to protect your cloud-stored files. Think of it as a digital safe for your data; you put your files in, and what comes out is a jumbled mess that only you can unscramble. Cryptomator is open-source, meaning its source code is available for anyone to scrutinize, lending an extra layer of credibility to its security claims.
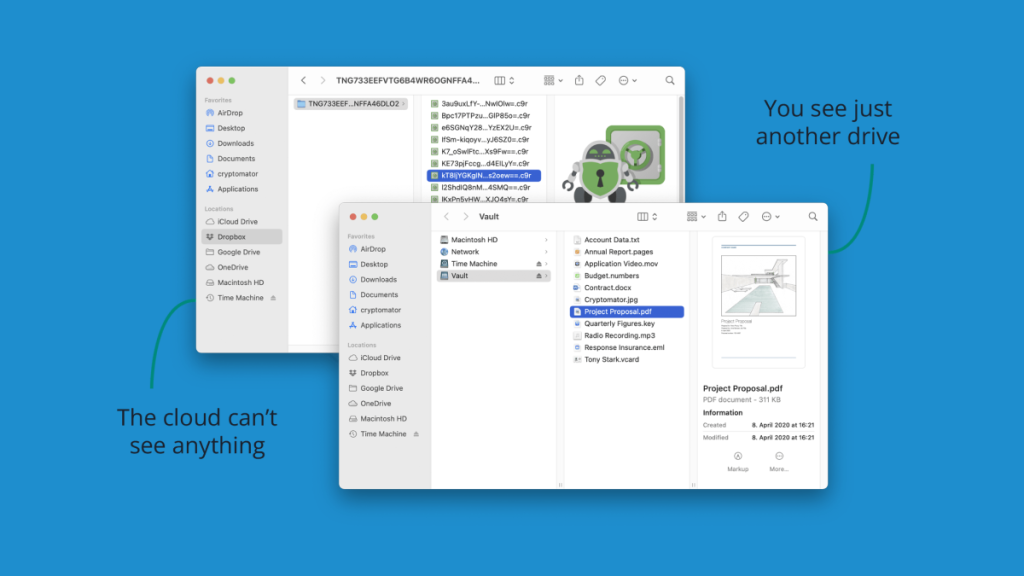
Let’s dive into the how-to of it all. You install Cryptomator on your computer, and it integrates directly with your cloud storage folder—be it Dropbox, Google Drive, or any other service. Then, you create a virtual drive through Cryptomator’s user interface, sort of like making a new folder. This drive appears alongside your C: drive, your USB sticks, and so on. Anything you drag and drop into this drive is automatically encrypted before it leaves your computer and heads to the cloud.
Use Cases
- Personal Documents: Got tax returns or medical records? Encrypt these sensitive documents before uploading them.
- Business Files: If you’re a freelancer dealing with client contracts or proprietary information, Cryptomator ensures that only you and your client can access the material.
- Photos: Your memories are yours alone. Encrypt your photo albums before sending them skyward to the cloud.
- Code Repositories: While services like GitHub offer private repos, an extra layer of security doesn’t hurt.
- Shared Drives: If you and a group are sharing a cloud folder for a project, Cryptomator can ensure that outsiders won’t decipher the folder’s contents even if they gain access.
Why is this particularly relevant? Simple. Security breaches happen. Imagine your cloud provider gets hacked, or you accidentally leave yourself logged in on a public computer. With Cryptomator, unauthorized eyes see nothing but gibberish when they look at your files. It’s like having a reinforced steel door on a straw house; even if someone breaks into the house, getting through that door is another challenge altogether.
In essence, Cryptomator adds an armor-clad layer of security to your cloud-stored files, making sure they’re for your eyes only.
Picocrypt
Picocrypt is a file encryption utility that aims for simplicity and robust security. Developed as an open-source project, its transparent codebase offers a clear view of its workings, a reassuring trait for the security-conscious.
At its core, Picocrypt encrypts files to keep them secure from unauthorized access. Say you’ve got confidential business files or personal photos you’d want to keep away from prying eyes. Picocrypt transforms these files into unreadable data unless someone has the correct key or password to decrypt them. It’s akin to turning your readable diary entries into an indecipherable code.
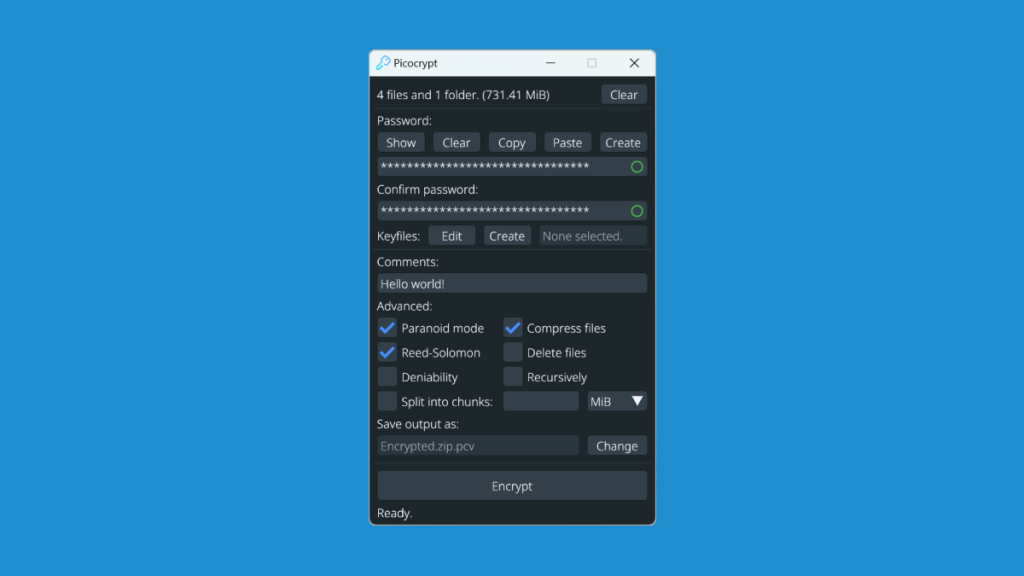
Why Choose Picocrypt?
- User-Friendly: Picocrypt sports a minimalistic interface that does away with the technical jargon. It’s like your friendly neighborhood cafe where everyone knows your name; approachable, no frills.
- Strong Encryption: Built around cryptographic algorithms like Argon2 and XChaCha20-Poly1305, Picocrypt offers military-grade encryption. Think of it as the Fort Knox of file encryption—nearly impenetrable.
- File Integrity: One unique feature is its emphasis on file integrity. Alongside encrypting your files, it also ensures they haven’t been tampered with during the encryption or storage process. It’s as if your security guard also performs quality checks.
Use Cases
- Personal Data: If you’re traveling and using public Wi-Fi, you’d want to encrypt sensitive data—be it tax documents or a novel you’re working on.
- Business Files: Working on a confidential project? Picocrypt ensures that the important files are accessible only to the team members with the correct key.
- Secure Sharing: Need to send sensitive information via email or cloud storage? Encrypt it first with Picocrypt, and then share the key separately for added security.
In summary, Picocrypt offers a straightforward yet highly secure method for encrypting files. Whether it’s to safeguard personal data or to ensure the confidentiality of work-related files, Picocrypt serves as an efficient and user-friendly tool. So, is Picocrypt the silver bullet for all your file encryption needs? While no software can claim to be foolproof, it comes strikingly close.
Hat.sh
Hat.sh is an open-source, web-based file encryption and decryption tool that operates entirely in your browser. This means no files are sent to a remote server for processing, providing an added layer of security. Built on top of modern cryptographic libraries, it utilizes the ChaCha20-Poly1305 encryption algorithm, a respected industry standard. If you’re into details, it’s worth mentioning that ChaCha20-Poly1305 is authenticated encryption that provides both data confidentiality and integrity.
So, what’s the real-world application here? Let’s say you’ve got some sensitive documents—financial records or a draft of an unreleased project—that you need to share with a colleague. You could just send these over email, but there’s always the risk that the email could be intercepted or the files mishandled. Hat.sh ensures that the file you’re sharing is encrypted before it leaves your computer. You then share the encrypted file via your preferred method—email, cloud storage, what have you—along with a decryption key that the receiver will use to unlock the file. Important note: You should share the decryption key through a separate, secure channel, like an encrypted messaging app, for maximum security.
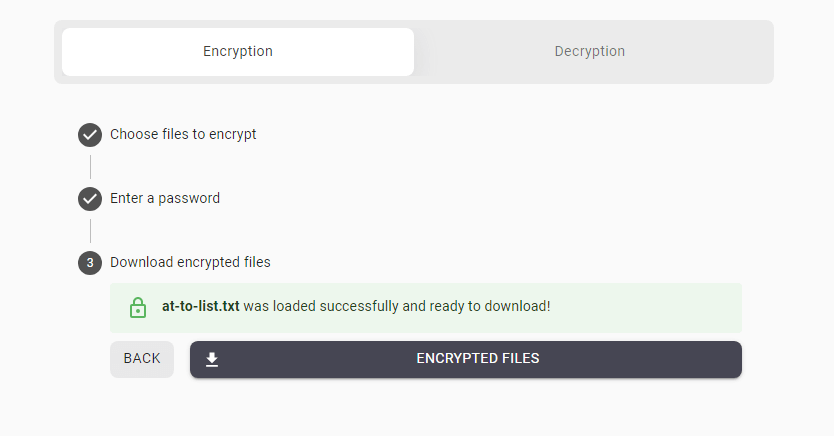
One could ask, why not just use a full-fledged encryption program? Well, Hat.sh simplifies the process considerably. There’s no software to download, no lengthy setup, and no strings attached. It’s a no-fuss, user-friendly solution, making encryption accessible to those who might not be well-versed in the complexities of data security. Plus, being browser-based, it’s platform agnostic. Whether you’re on a Windows PC, a Mac, or even a Linux workstation, your browser is all you need.
What sets Hat.sh apart? Aside from its ease of use, it also allows you to encrypt multiple files at once, bundled into a ZIP archive. It’s particularly useful when you’re dealing with a project that has multiple associated files, and you want to ensure that all of them remain secure during transit.
However, no tool is a panacea. Hat.sh is a great utility for specific use-cases, but it’s not a replacement for full-disk encryption or a comprehensive security strategy. Think of it as a secure briefcase for your digital files—one that’s remarkably easy to use and doesn’t require you to be a cryptography expert.
Summary
In wrapping up, we’ve taken a deep dive into the world of file encryption software, breaking down how it works and why it’s essential in today’s environment. From understanding algorithms to the intricacies of encryption keys, it’s clear that securing your data is a nuanced task best left to reliable tools.
Whether you’re a casual user wanting to protect personal photos and documents or a business aiming to secure confidential information, opting for a high-quality encryption solution is a non-negotiable. Armed with the insights from this article, you’re now better equipped to make an informed choice and give your data the fortress it deserves. After all, in the realm of digital security, it’s better to be safe than sorry.
