In a world where data leaks and cyber espionage regularly make headlines, the quest for secure communication has never been more pressing. It’s not just a matter of keeping your weekend plans with friends under wraps; it’s about safeguarding your financial information, your business strategies, and in some cases, even your personal safety. It’s also about steering clear of the prying eyes of advertisers, third-party data harvesters, and yes, sometimes even governments.
But what does ‘secure’ even mean when it comes to instant messaging, voice calls, or video chats? Is end-to-end encryption the final word, or is there more to the story? How does anonymity fit into the picture, especially if you’re trying to avoid the scrutiny of oppressive regimes? And what about group communication for work or social causes, where the stakes might be even higher?
This article aims to provide clear, actionable insights into the world of encrypted messengers, dissecting the nuances across four key categories:
👉 Click on any of the categories to jump directly to that part of the article!
- Private & Secure Messaging
- Anonymous Instant Messaging via Tor
- Private and Secure Team Chats
- Encrypted Video & Voice Messengers
Whether you’re a concerned individual, a privacy advocate, or a team leader at work, buckle up. We’re diving deep into a realm where messages disappear, identities are masked, and voices are mere echoes that don’t leave a trace.
📲 Private & Secure Messaging
When it comes to personal communication, most of us want an ironclad guarantee of privacy. Enter the realm of private and secure messaging apps, where encryption isn’t just a fancy add-on but the foundational pillar. Whether you’re a journalist protecting sources or just an average Joe shielding grocery lists, these apps provide the digital equivalent of a sealed envelope in a world of postcards.
Signal
Signal is a messaging app that has gained a solid reputation for its focus on privacy and security. Developed by the Signal Foundation, this open-source platform employs end-to-end encryption to secure all forms of communication—text, voice, and video. You might be wondering, “What’s the big deal with end-to-end encryption?” Simply put, it ensures that only you and the person you’re communicating with can read or listen to what is being sent. Even Signal can’t access your conversations.
How does Signal achieve this level of security? It employs the Signal Protocol, a cryptographic method co-created by Moxie Marlinspike, the app’s co-founder. This protocol is also used by other major messaging platforms like WhatsApp, but what sets Signal apart is its transparent approach. Because it’s open-source, anyone can scrutinize its code to confirm that there are no backdoors or vulnerabilities—a transparent move that has won it the trust of security experts.
Notably, Signal offers a range of features that go beyond basic encrypted messaging. For example, it allows for disappearing messages, which vanish after a set time, and it also provides a “sealed sender” option that hides the sender’s identity. You can even use the app to make encrypted group calls, making it versatile for both personal and professional use.
Is it user-friendly? Absolutely. The app’s interface is clean and intuitive, so you won’t need a degree in computer science to navigate it. But what about compatibility? You can use Signal on various platforms, including Android, iOS, and desktop.
What’s the catch? Well, some might argue that Signal’s rigorous security measures can sometimes get in the way of convenience. For instance, if you lose your phone and haven’t backed up your Signal messages, you’ll lose them for good. But for many, that’s a small price to pay for such high-level security.
So, should you ditch your current messenger for Signal? If privacy is a top concern, the answer is likely yes. It’s a tool built not just to facilitate communication, but to protect it at all costs.
Status
Status is a mobile-first, peer-to-peer messaging platform that places a significant emphasis on user privacy and data security. Unlike many of its centralized counterparts, Status employs the Ethereum blockchain to provide secure communications. But why does this matter?
Centralized services can be a treasure trove of data just waiting to be exploited or subpoenaed. By contrast, Status decentralizes the process, removing any central entity that could potentially be a single point of failure. Your messages aren’t stored on some remote server; they exist only on your device and the devices of your intended recipients. That means there’s no central database for hackers to target or authorities to subpoena.
The idea is simple: your conversations should be between you and the person you’re talking to, without any room for eavesdropping.
Status isn’t just about messaging, though. It doubles as a sort of decentralized web browser for the Ethereum network, allowing you to access decentralized apps (dApps). This multitasking approach might be a little ambitious, but it’s an interesting avenue for those looking to escape the clutches of centralized web services.
One downside? Usability can sometimes take a hit when you prioritize security to this extent. The user interface and experience might not be as smooth as what you’d find on more mainstream platforms. But for those who are willing to navigate a steeper learning curve, the rewards in terms of privacy and security are tangible.
So, what’s the final verdict on Status? If you’re a privacy hawk or simply someone keen to explore the frontier of decentralized technology, Status offers a compelling package. It might not be your go-to for casual chats with grandma—unless she’s a crypto enthusiast—but it’s a robust option for secure, encrypted conversations.
Session
Session is an end-to-end encrypted messenger designed to protect your privacy and offer secure communication channels. Developed by the Loki Foundation, this app doesn’t require a phone number or email to sign up. Instead, it generates a unique Session ID, decoupling your identity from the messages you send. So, what sets it apart from the Telegrams and the Signal apps of the world?
For starters, Session uses the Onion routing protocol to make sure your metadata—basically the digital paper trail that most other messengers leave behind—is also encrypted. This is a game-changer. You can think of it as the digital equivalent of shredding your physical mail’s envelope before throwing it away.
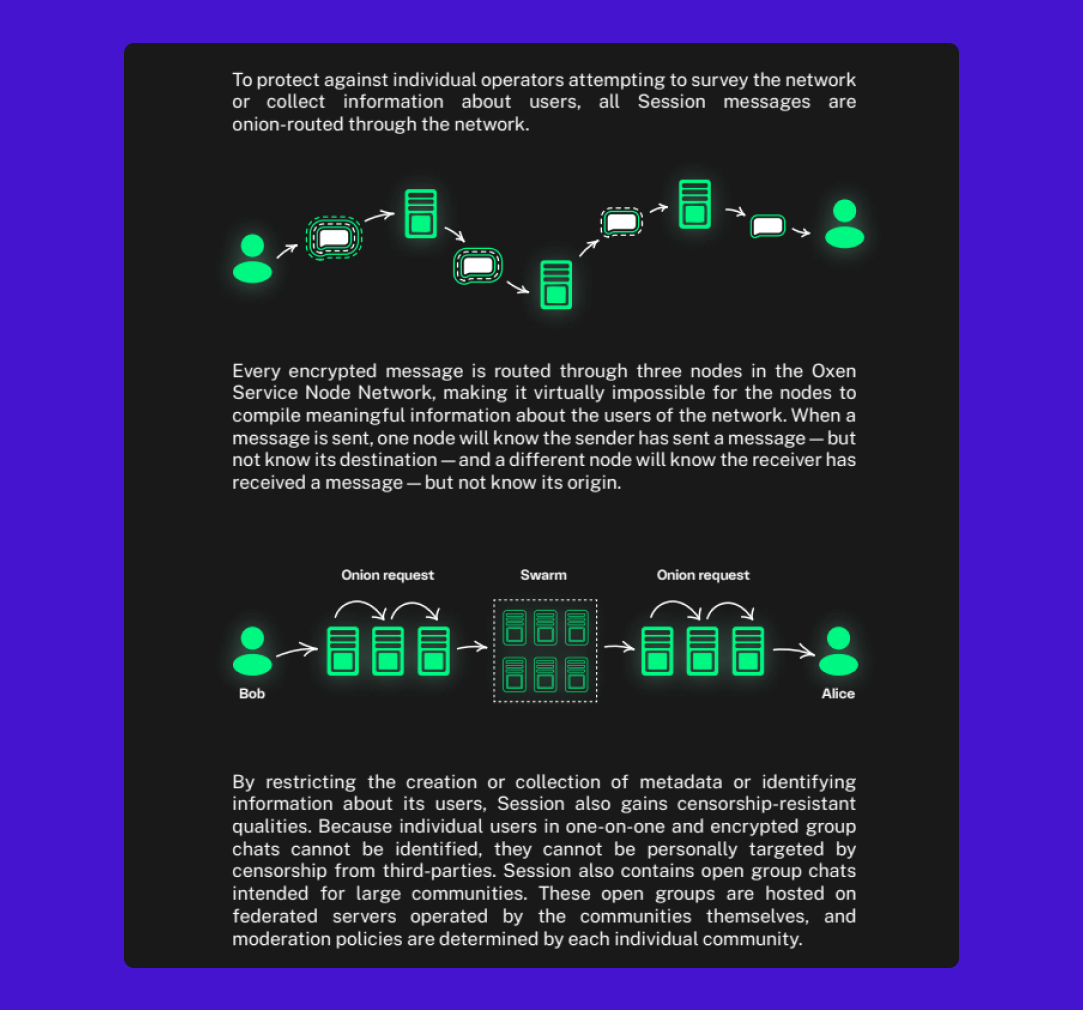
Another noteworthy feature is the decentralized server architecture, which breaks away from the conventional central-server model. Instead, it leverages blockchain technology to distribute data across multiple nodes. It’s like a network-wide game of keep-away with your data, making it harder for any single entity to compromise the information. Plus, this decentralized approach lowers the risk of server outages, making the app more resilient and reliable.
Session supports text chats, voice messages, and even encrypted group calls. It’s available on Android, iOS, Windows, macOS, and Linux, offering a seamless experience across devices. However, it’s worth mentioning that Session is relatively new and still in active development. While it promises high-security features, keep in mind that it hasn’t undergone the extensive third-party audits that established messengers like Signal have.
In summary, Session offers an intriguing alternative in the secure messaging space, covering not just the content but also the often-overlooked metadata. It’s not just about what you say; it’s also about leaving no trace that you ever said it.
Threema
Threema, a Swiss-based messaging app, has been capturing attention for its focus on privacy and secure communication. Unlike many competitors that offer end-to-end encryption as an add-on, Threema was engineered with security at its core. This begins at registration: no phone number or email is required, reducing the chances of identity linking. A randomly generated Threema ID serves as the user identifier, which ensures a layer of anonymity right off the bat.
But how secure is it, really? Threema employs the NaCl cryptography library, utilizing the strong 256-bit elliptic curve cryptography. This, combined with forward secrecy, makes it exceedingly difficult for anyone to intercept and decipher your messages. Voice and video calls? Also encrypted. Group chats? You guessed it, encrypted as well. Moreover, messages are deleted from the servers once delivered, leaving no digital trace.
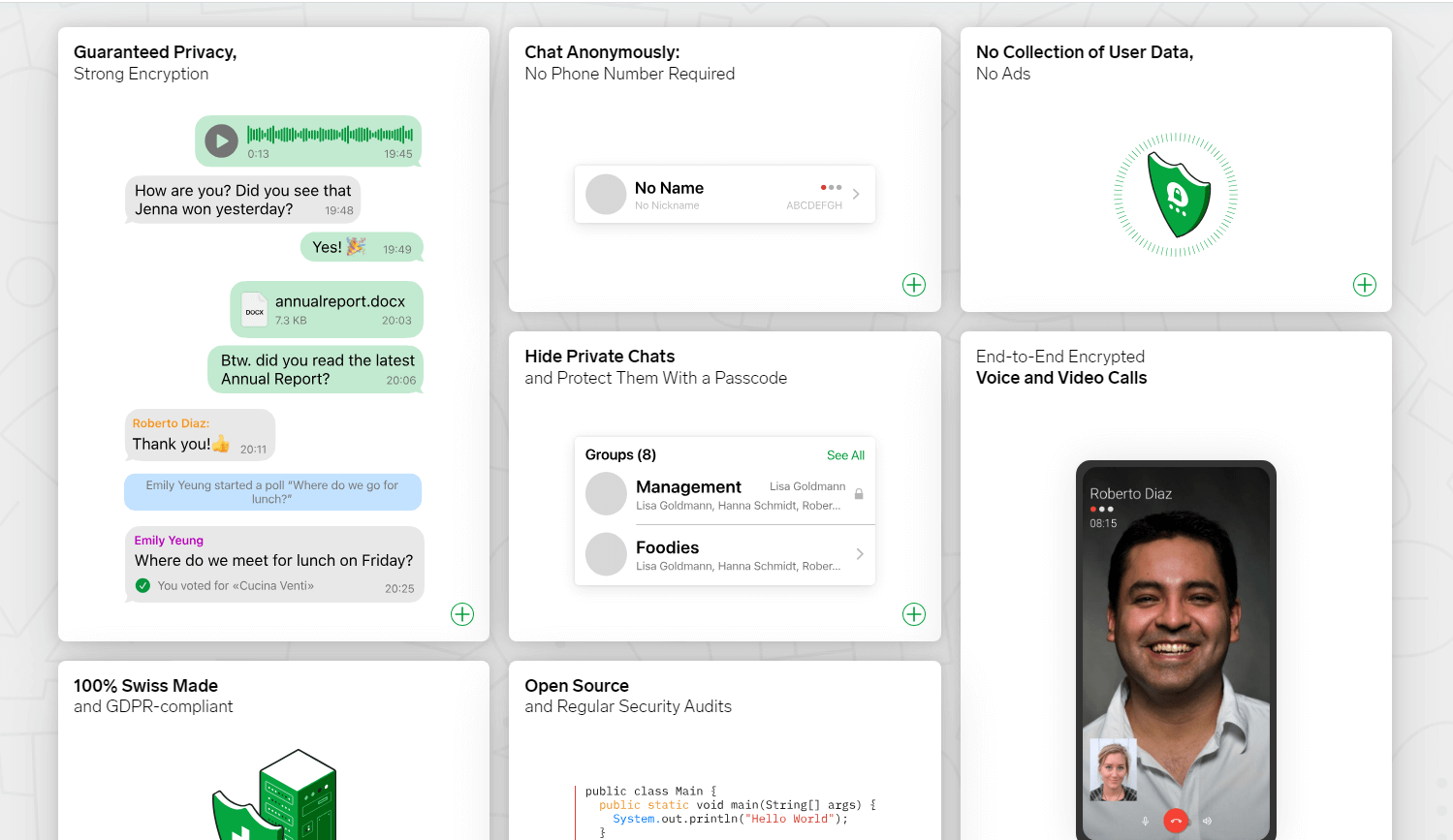
How does Threema stack up in terms of features, though? Despite its security-oriented architecture, the app doesn’t skimp on user experience. It supports text messages, voice and video calls, file sharing, and even offers features like polls. All of this operates under the same robust encryption protocols.
However, there’s a catch. Unlike many popular messaging apps, Threema is not free. There’s a one-time fee for downloading the app. Some might balk at this, but consider it a straightforward business model: you pay for the service, so you’re not the product. The absence of ads and the assurance that your data isn’t being monetized may be a compelling trade-off for those serious about privacy.
If privacy is a top concern, Threema makes a compelling case for itself. It offers strong encryption protocols, requires no personal identifiers, and promises not to store your messages. The cost might be a hurdle, but it’s a small price to pay for digital peace of mind.
Delta Chat
Delta Chat stands as a unique entrant in the arena of secure messaging apps. What sets it apart? It leverages email to power its chat ecosystem. That’s right—no proprietary server labyrinth to navigate. Your email account is your ID, and your existing email server functions as the chat server. It sounds almost archaic in an age flooded with standalone messaging apps, doesn’t it? But here’s the kicker: this setup could actually fortify your data security.
How does it accomplish that? Delta Chat uses end-to-end encryption, courtesy of the Autocrypt standard. Messages are encrypted on your device and decrypted on the recipient’s end, making it nearly impossible for anyone in between to eavesdrop. Given that you’re utilizing email servers that are often safeguarded with robust security measures, it adds another layer of protection to your communications.
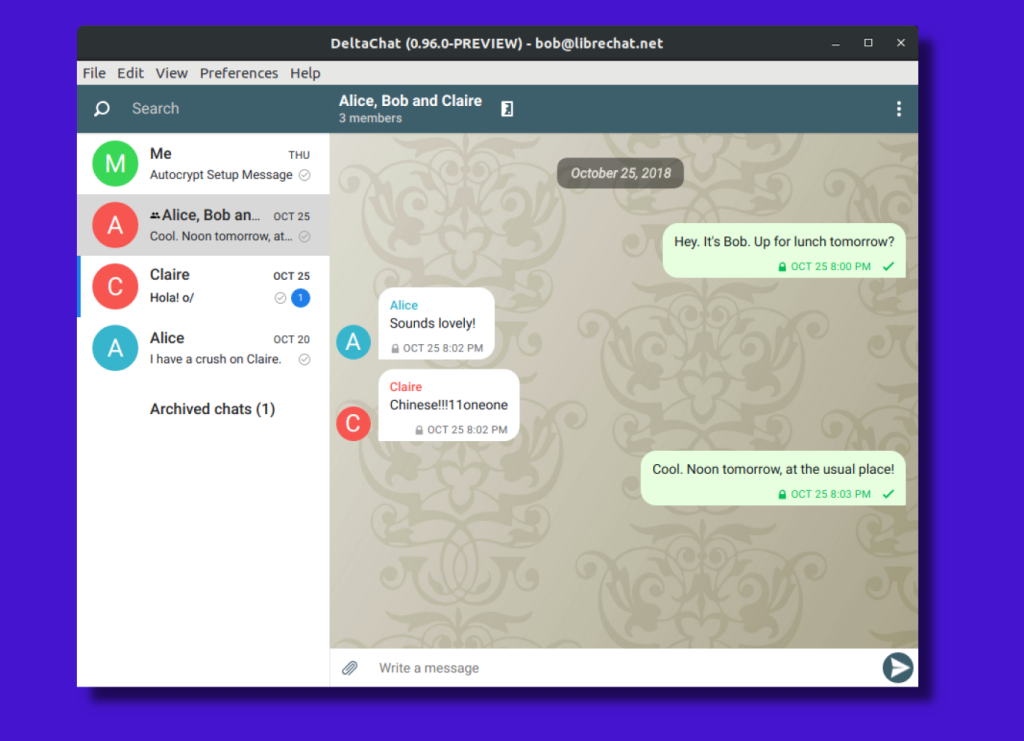
But what about user experience? Rest assured, it mirrors the typical chat interface you’re accustomed to. Your emails get transformed into a chat-like format, complete with real-time syncing and instant notifications. There’s even support for voice and video calls, although it’s worth mentioning that these features are still in the experimental phase.
Is Delta Chat for everyone? Probably not. The reliance on email could be a sticking point for some, especially those not keen on mixing their email and chat correspondence. Moreover, both parties need to use Delta Chat to take advantage of end-to-end encryption, though regular emails can still be sent and received. But for those who prioritize security and appreciate the versatility of using their email for chats, it presents an intriguing option.
😎 Anonymous Instant Messaging via Tor
So you’re not just dipping your toes into the privacy pool; you’re ready to dive into the deep end. Tor-based messaging apps are your snorkeling gear in this sea of anonymity. Think of them like the James Bond of digital conversations, existing in a labyrinth of encrypted tunnels. Ideal for whistleblowers, activists, or anyone who needs to keep their identity under wraps, these apps are where you can talk without leaving footprints.
Speek!

Speek distinguishes itself as a messaging platform that’s not just secure but also anonymous and censorship-resistant. Let’s cut to the chase: What makes it such a standout?
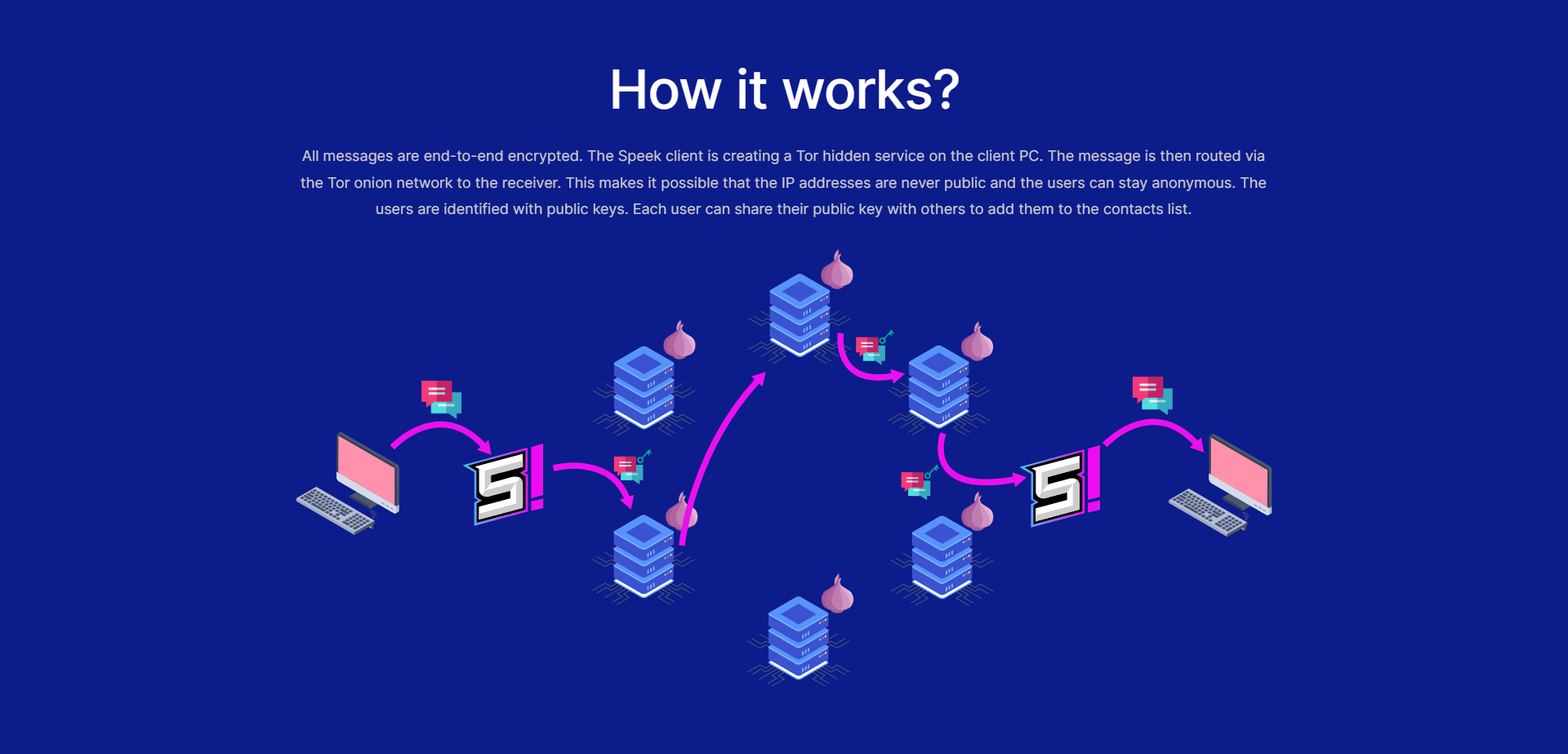
The technology is where Speek really shines. Unlike other encrypted messaging apps that route messages through centralized servers, Speek goes serverless. How? By leveraging the Tor network. When you send a message via Speek, it creates a Tor hidden service right on your PC, ensuring that the message routes through the onion network. This means your IP address remains unknown, preserving your anonymity.
There’s no metadata saved, and the messages are end-to-end encrypted. The sender and the receiver are identified solely through public keys, not by phone numbers or user IDs.
Alright, what about the features? Beyond messaging, Speek offers secure file sharing. Want to send a confidential document or a sensitive image? Speek’s got you covered. This makes it particularly useful for not just personal conversations but also for professional settings where confidentiality is paramount.
How does it stack up against big names like WhatsApp, Telegram, or Signal? In terms of security, Speek claims to have them all beat. That’s a tall order, but they back it up. Because it’s decentralized, serverless, and routes messages through Tor, Speek doesn’t even collect metadata. This offers a level of anonymity and security that centralized services can’t match.
But let’s not forget the human element. What if you accidentally leave the app running? No worries. Speek automatically deletes all messages from your device as soon as you close the app. It’s designed to be as ephemeral as a spoken conversation in real life. Plus, the absence of any censorship mechanism means it’s practically impossible for anyone to block or ban your messages.
Briar

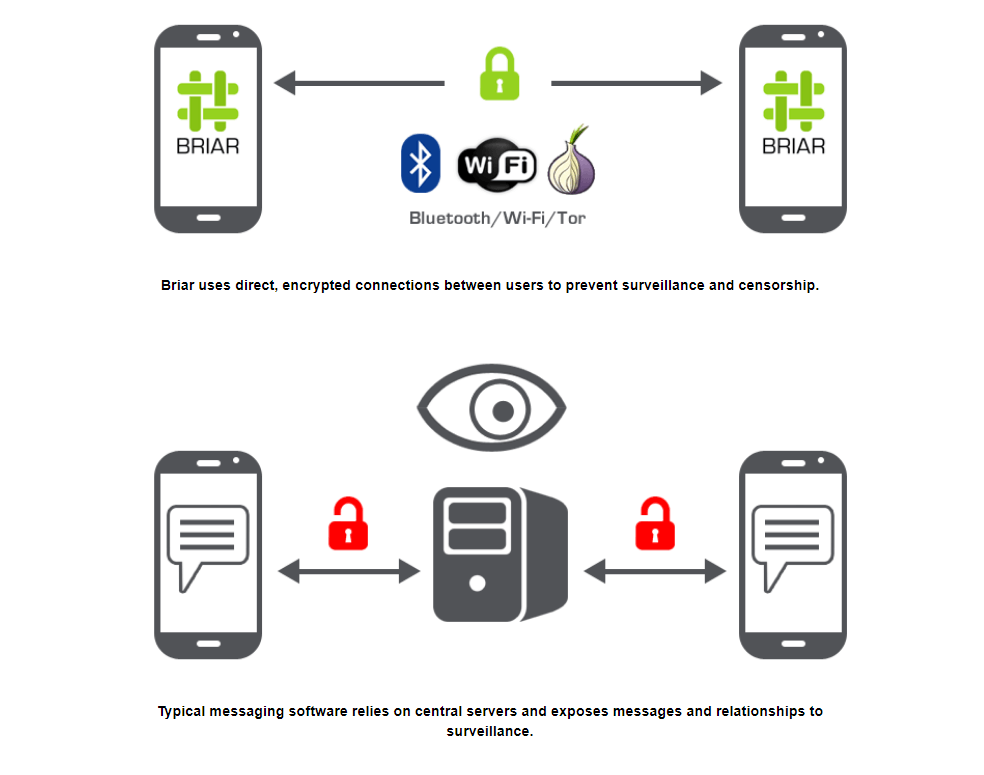
Briar is a messaging app designed with a unique focus on privacy and secure communication. Unlike most mainstream messaging platforms that rely on centralized servers, Briar operates on a peer-to-peer architecture. What does this mean for the user? In short, there’s no middleman to snoop on your conversations.
The messages go directly from one device to another, either through Bluetooth, Wi-Fi, or over the Tor network. So even if you’re discussing something as mundane as your dinner plans or as sensitive as whistleblowing, your messages are designed to stay in a closed loop.
One noteworthy feature is its resilience to network failures. Ever been in a situation where a centralized service goes down and suddenly you’re cut off from your contacts? Briar sidesteps this issue by allowing offline messaging. How so? If your friend is within Bluetooth or Wi-Fi range, the messages are transferred directly, bypassing the need for an internet connection altogether. This makes it ideal for situations where network infrastructure is either unreliable or compromised.
Now, you might wonder, how secure can this really be? Briar takes encryption seriously. Messages are end-to-end encrypted, making it extremely difficult for anyone, even those with considerable resources, to intercept and read your messages. The app uses well-established cryptographic protocols, so it’s not some home-brewed formula that hasn’t stood up to scrutiny.
But let’s address the elephant in the room: user experience. With all these security features, is Briar a chore to use? The answer is a measured ‘no’. While it doesn’t offer the snappy, polished interface of some of its less-secure competitors, it remains user-friendly. Keep in mind, however, that due to its stringent security measures, features like message backup and multi-device support aren’t present. For many, that’s a small price to pay for the level of security it offers.
Ricochet Refresh
Ricochet Refresh is an intriguing player in the secure messaging space. It employs a peer-to-peer (P2P) model using Tor onion services. Why is this a game-changer? Well, for one, there’s no central server housing your messages, which eliminates a crucial point of failure. This is in contrast to mainstream messaging apps, which often store your chat logs on centralized servers, making them susceptible to hacks or government subpoenas.
The fundamental mechanism of Ricochet Refresh is clever yet straightforward. When you use this application, you get a unique .onion address, making you essentially a Tor hidden service. Want to talk to a friend? You’ll connect directly to their .onion address, bypassing the need for middlemen entirely.
This direct connection ensures that no one can snoop in on your conversations, even if they wanted to. However, it’s important to note that this setup does require both parties to be online simultaneously for a conversation to happen—think of it like a walkie-talkie rather than voicemail.
But here’s a kicker: Ricochet Refresh also ditches metadata, that silent snitch that can reveal when you sent a message and to whom, even if the message itself is encrypted. Because the application uses Tor, your IP address is obscured, and because it’s P2P, there’s no server to log who’s talking to whom and when.
One downside? The interface and user experience are far from glamorous. It’s functional but lacks the bells and whistles that make apps like Signal and Telegram user-friendly. Moreover, because it leverages Tor, it might be slower than other services. But for those who prioritize privacy above all, these may be minor quibbles.
So, is Ricochet Refresh the Fort Knox of secure messaging? Well, it’s hard to say definitively, but it’s built on some solid security premises. The project is open-source, inviting the scrutiny and contributions of developers who want to make it even stronger. And while it might not have a billion-dollar company backing it, sometimes the underdogs offer the most robust solutions, don’t you think?
Cwtch
Cwtch takes a different approach to secure messaging than many of its counterparts, like Signal or Telegram. Originating from the Welsh word for “a hug that creates a safe space,” Cwtch is less about individual privacy and more about group privacy. It’s a peer-to-peer platform, which means there’s no centralized server housing your messages. This decentralized approach makes it difficult for anyone to compromise the system as a whole.
So, how does Cwtch accomplish this? It leverages onion routing, the same technology that powers Tor. Messages are encrypted and then routed through multiple nodes, obfuscating both sender and receiver. It’s not just about hiding what you’re saying but also hiding who is talking to whom. This anonymity set provides a level of security that’s appealing for anyone keen on avoiding surveillance.
But here’s a crucial point: Cwtch is not designed for everyone. It’s built for people who have a higher threat model and require more robust security measures. Are you an activist, journalist, or just someone genuinely concerned about privacy at a granular level? Then Cwtch could be the platform for you. It lacks some of the user-friendly features that you’ll find in mainstream apps—no emoji reactions or animated GIFs here—but what it sacrifices in frills, it gains in secure functionality.
Is Cwtch perfect? No secure system is. It’s still a work in progress, and like any other software, it can be subject to vulnerabilities. But the key takeaway here is that Cwtch aims to offer a more secure space for collective communication, not just for one-on-one chats. The question isn’t merely whether you should use it but whether its unique approach to privacy aligns with your own needs and concerns.
Tox
Tox is a secure, decentralized messaging platform that emerged a few years ago, spurred by concerns over widespread digital surveillance in the wake of Edward Snowden’s revelations. The platform aims to offer users a way to communicate without having to rely on centralized servers, which are often vulnerable to raids, shutdowns, or coerced data turnover.
So what can Tox do? For starters, it’s not just about text messages. Tox offers a comprehensive suite of communication features: encrypted voice and video calls, file sharing, and even screen sharing. Unlike many other big-name services, Tox provides all these features for free, devoid of advertising.
It’s noteworthy that Tox was created by its users, a community of developers fed up with the existing, invasive options. It’s developed by volunteers, with no corporate interests steering the wheel. The code is open-source, which not only means you can verify its security and modify it if you wish but also signifies that the software is free—both as in freedom and in price.
The encryption in Tox is robust, using well-regarded open-source libraries. End-to-end encryption is the default and sole mode of operation, and your identity is secured by your personal private key, which never leaves your computer. In essence, your conversations are visible only to you and the person you’re communicating with.
But what about the clients? Several independent Tox client projects exist, catering to a range of operating systems and interface preferences. Notable examples include qTox, which offers a feature-rich interface, and µTox, which is lightweight with minimal dependencies. For Android users, aTox is available, and for those who prefer terminal-based interfaces, Toxic is an option.
However, Tox does have its limitations. For instance, it doesn’t cloak your IP address while communicating with friends. But then again, the essence of a peer-to-peer network is to connect you directly with your contacts. Though it’s not foolproof, there are workarounds like tunneling Tox connections through Tor to add an extra layer of anonymity.
💬 Private and Secure Team Chats
You’ve got a team, and you’ve got secrets—not the “office gossip” kind but sensitive project information that needs to stay in-house. In a world where business espionage isn’t just the stuff of spy novels, you need a team chat app that’s more Fort Knox than open forum. It’s about creating a space where collaboration thrives but prying eyes hit a brick wall.
Rocket.Chat
Rocket.Chat is an open-source communication platform designed to facilitate secure conversations for organizations and teams. Its architecture allows for self-hosting, which puts the control of data firmly in the hands of the organization using it. This is a noteworthy contrast to proprietary solutions, where data often resides on external servers subject to different privacy laws and potential vulnerabilities.
So, what makes Rocket.Chat stand out when we’re talking secure messengers? First, its end-to-end encryption is implemented for both one-on-one and group conversations, covering chat, voice, and video. The encryption is device-based, meaning that decryption keys stay local and aren’t stored on the server.
Trust is hard to gain but easy to lose, right? Well, the open-source nature of Rocket.Chat means that its code is publicly available for scrutiny, allowing anyone to audit the software for potential security issues.
But how user-friendly is it? Is the interface something your grandma would look at and run for the hills? Fortunately, Rocket.Chat offers an intuitive user interface that doesn’t require a steep learning curve. Features like screen sharing, voice messages, and file sharing are neatly integrated, making the platform accessible for users of all tech-savviness levels.
So, is Rocket.Chat the be-all and end-all of secure messaging platforms?
Not exactly. While the platform offers robust security features, the self-hosting model might not be ideal for everyone. Smaller teams without dedicated IT support may find it challenging to manage the server, leading to potential security lapses if not handled correctly.
Revolt Chat
Revolt Chat emerged as an open-source platform offering chat, voice, and video functionalities, aimed at providing a secure and private experience for its users. Developed in the Rust programming language, it focuses on speed, security, and a straightforward user interface. What sets it apart?
Firstly, encryption is baked into its DNA. Revolt uses end-to-end encryption to protect your text messages and voice/video calls, ensuring that only the recipient can read or listen to them. As it’s open-source, experts and enthusiasts alike can scrutinize its code to spot vulnerabilities. A robust security model? Absolutely.
So, what about features? Revolt doesn’t skimp here either. Expect all the usual suspects like group chats, file sharing, and reactions. Plus, the user interface is nothing to sneeze at—clean, intuitive, and relatively easy on the eyes. It offers native apps for multiple platforms, making it accessible whether you’re glued to your Android or partial to your MacBook.
Now, you might be thinking, “Does this add another layer of complexity?” Not really. Revolt Chat aims to be as user-friendly as possible, knowing full well that a secure platform is useless if people find it too cumbersome. It hits that sweet spot where simplicity meets functionality, making it a strong contender in the arena of secure communication platforms.
Finally, why should anyone care? In a world where data breaches are more common than we’d like to admit, a tool that prioritizes user privacy isn’t just nice to have—it’s a necessity. And Revolt delivers on that front, offering a secure haven for your digital conversations. So, is Revolt Chat worth considering for your secure communication needs? The answer leans heavily towards a yes.
Element
Element is an open-source, decentralized messaging platform designed with privacy and security at its core. It leverages the Matrix protocol to ensure end-to-end encryption, allowing for secure text, voice, and video communication. What sets Element apart from the crowd? Its commitment to interoperability, for one. The platform lets you chat or call not just other Element users, but also those on different Matrix-based services.
Why should someone care about decentralization in a messaging app, you ask? The absence of a central server means there’s no single point of failure—or control. Your data isn’t stored in one massive hub, making it less susceptible to hacking or corporate overreach.
While other mainstream platforms promise security, they often come with caveats, such as metadata collection. Element offers a transparent approach: users can actually see the encryption algorithms at work if they’re so inclined.
But is it user-friendly? Absolutely. Element’s interface strikes a balance between advanced features and usability. Whether you’re setting up a multi-party video conference or simply want to send a text message, the process is straightforward. And if you’re running a business, there’s Element for Teams, which brings an additional layer of administrative features and enterprise-grade security.
The app is versatile, too. It’s cross-platform, available on Android, iOS, Windows, macOS, and Linux. That means you’re not shackled to any particular ecosystem—a breath of fresh air in an increasingly siloed tech world.
In summary, Element provides a secure, encrypted, and decentralized platform that doesn’t skimp on features or usability. It stands as a robust alternative to centralized systems, giving users more control over their data while maintaining a sleek, user-friendly experience.
📹 Encrypted Video & Voice Messengers
Remember when video calls felt like a sci-fi future? Now they’re an everyday reality, but with that convenience comes vulnerability. Your face, your voice, the room you’re in—all can be hijacked in less secure platforms. But there’s a solution: encrypted video and voice messengers that act like VIP rooms with a strict guest list. Imagine these apps as your personal security detail, ensuring that your calls are for your ears and eyes only.
Jami
Jami, formerly known as Ring, presents itself as a robust player in the encrypted communications game. Born from the open-source ethos, it’s engineered for those who take their digital privacy seriously. Why open-source, you ask? Well, it allows any user or developer to scrutinize the code for potential vulnerabilities, essentially crowd-sourcing the security aspect. It’s like having a neighborhood watch for your software.
So, what does Jami offer? Let’s start with the basics: text chats, voice calls, and video conferences. All of these are encrypted end-to-end, meaning only you and the person you’re communicating with can decipher the content. There’s no middleman, and there aren’t any servers storing your chats. You connect directly to your contacts, akin to a digital handshake that bypasses the usual social pleasantries and gets straight to confidential chatting.
And speaking of bypassing—Jami sidesteps the need for a centralized server. This decentralized approach not only aligns with the ethos of data privacy but also eliminates a single point of failure. You know how, in heist movies, there’s always that one vault that if cracked, gives access to all the treasures? Centralized servers are like that vault. Jami doesn’t have one, making it more resilient against attacks.
Another perk? You’re not required to give out personal information like your email or phone number to sign up. Your identification on Jami is a unique username, which can be as descriptive or as cryptic as you want. This feature makes it more difficult for data miners and snoopers to piece together your identity.
Linphone
Linphone is an open-source VoIP application that offers end-to-end encryption, a key feature for anyone concerned with securing their communications. Originating as a project in 2001, Linphone provides a range of communication options including voice calls, video calls, and text messaging. So, what makes Linphone tick in the realm of secure and encrypted messengers?
Firstly, the app uses Session Initiation Protocol (SIP), a widely accepted protocol for voice and video communication. This ensures compatibility with a broad range of other VoIP services and hardware. But let’s talk security. Linphone employs the ZRTP protocol for end-to-end encryption, safeguarding both voice and video calls.
For the uninitiated, ZRTP essentially puts up a cryptographic wall between your conversation and potential eavesdroppers. The protocol is designed to resist even “man-in-the-middle” attacks, making it tough for intruders to decode your communication even if they can intercept it.
Text chats are secured using Transport Layer Security (TLS), a well-recognized standard also used to protect web traffic. So whether you’re gossiping about last night’s game or sharing sensitive business info, your text messages are covered under Linphone’s security umbrella.
And the best part? Being open-source, Linphone invites scrutiny from developers and security experts alike, making its encryption more transparent than proprietary options. Open-source software, after all, can be like a neighborhood watch for code; more eyes can mean fewer vulnerabilities.
But wait, is Linphone for everyone? It offers robust security measures, but its interface might not be the most intuitive for those accustomed to more mainstream messaging apps. And because it adheres to SIP, setup can be a bit more technical than just downloading an app and punching in your phone number. The security benefits are there, but you may need to get your hands a bit dirty in the settings menu to reap them fully.
Linphone is available for Win, Android, iOS, Mac, and Linux.
Jitsi Meet
Jitsi Meet has recently implemented a key change: as of August 24th, the platform no longer allows for anonymous room creation. Users are now required to authenticate through an account—initially Google, GitHub, or Facebook. This change aims to curb misuse of the service.
Now, let’s refocus on Jitsi Meet as a secure and encrypted communications platform. End-to-end encryption remains one of its strongest suits. While Jitsi Meet’s server can theoretically access raw video streams, the architecture mitigates potential interception by third parties. If you’re looking for additional privacy, you can self-host a Jitsi Meet instance on your own server, which still remains an option.
Anonymity was a unique feature of Jitsi Meet, but that’s no longer the case. Users must now authenticate, which introduces a new layer of accountability but could be perceived as a drawback for those who value total anonymity. However, the commitment to encrypted communication remains unchanged, according to the platform’s recent blog post.
In terms of functionality, Jitsi Meet doesn’t skimp. The service includes features like background blur, speaker stats, and livestreaming options. Versatile enough for a casual catch-up or a professional webinar, the platform’s features have been designed to serve a variety of use-cases.
Being open-source also continues to be a major advantage for Jitsi Meet. The transparency of the code allows anyone to inspect it for vulnerabilities or suggest improvements. This openness is often viewed as a boon for security-focused individuals and organizations.
To sum up, the recent change in requiring account-based authentication marks a shift in Jitsi Meet’s approach to privacy and accessibility. However, its core attributes of encryption, self-hosting options, and open-source codebase still make it a solid choice for secure and encrypted communications.
Summary
In summary, the realm of secure and encrypted messaging is not a one-size-fits-all landscape. Privacy Messaging offers a secure haven for the everyday user concerned about data leaks and surveillance. Anonymous Instant Messaging via Tor provides an additional layer of anonymity, useful in high-risk situations or oppressive environments. Private and Secure Team Chats address the unique complexities and stakes of group communication in both professional and activist settings. Finally, Encrypted Video & Voice Messengers bring peace of mind to real-time conversations that can otherwise be easily intercepted.
So, what’s the bottom line? In a world where our data trails can be both an asset and a liability, choosing the right encrypted messenger is more than just a matter of preference—it’s a matter of security, freedom, and sometimes even justice. Regardless of which category you find yourself leaning towards, make sure to weigh the pros and cons, and to understand the limitations of each platform.
Remember, the most secure messenger is only as effective as your understanding of how to use it. Equip yourself with the knowledge, choose wisely, and communicate freely—just ensure that ‘freely’ also means ‘securely.’













