A severe exploit in GitLab, a prominent online DevOps platform utilized for collaborative software development, is currently being leveraged by hackers to hijack user accounts through password resets. The flaw, identified as CVE-2023-7028, enables hackers to redirect account password reset notifications to unauthorized email addresses.
Consequently, attackers can initiate a password reset for any user. This vulnerability has received a critical severity rating of 10.0 out of 10. Users who have enabled two-factor authentication (2FA) on their accounts are somewhat shielded; although their passwords may be reset, account access still requires verification through a second factor.
GitLab addressed the issue with patches released on January 11. Despite these fixes, data from the Shadowserver Foundation reveals that over a thousand GitLab setups remain exposed online, with around 350 located in the USA.
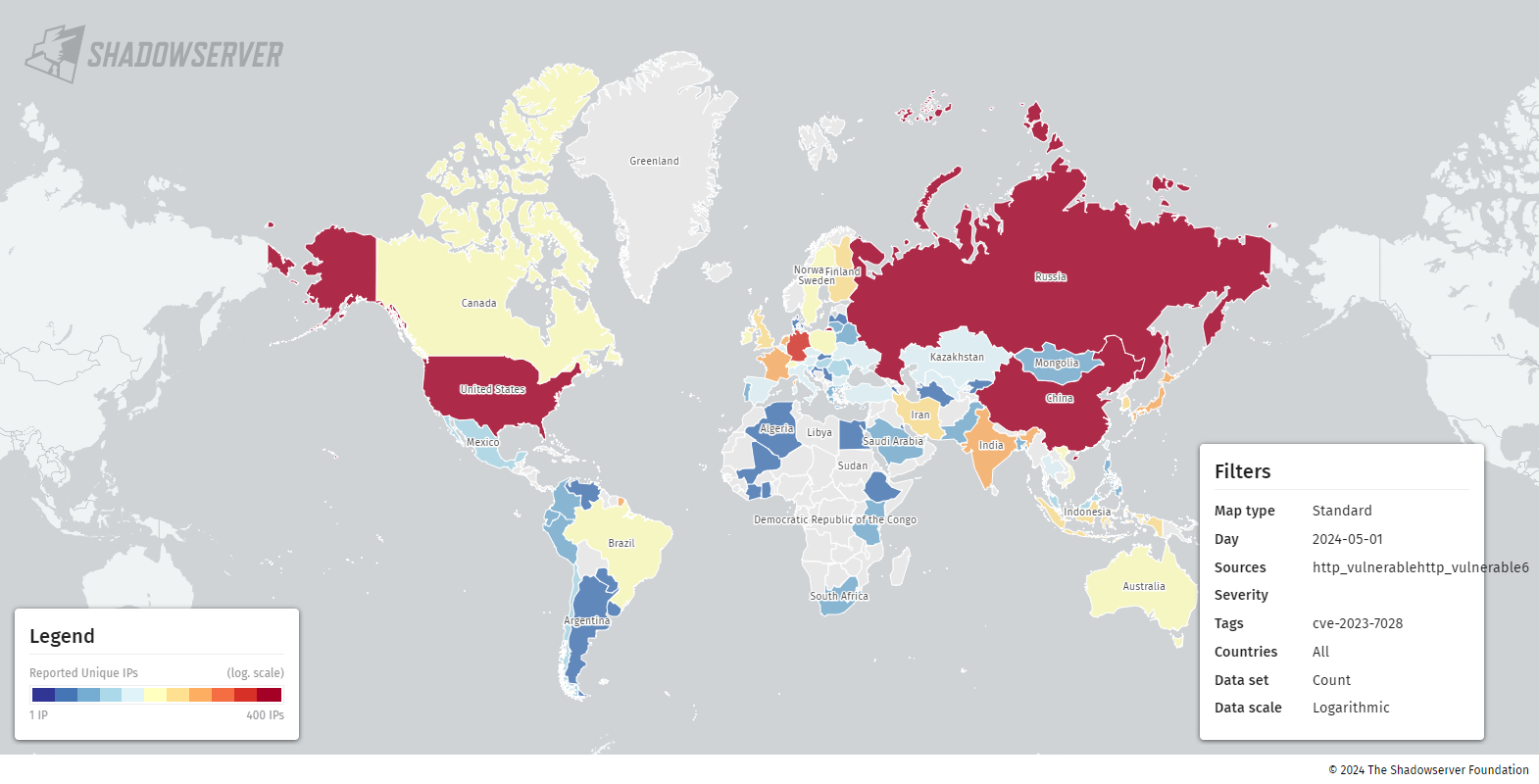
Initially, GitLab reported no known exploitations of this vulnerability. However, the Cybersecurity and Infrastructure Security Agency (CISA) within the US Department of Homeland Security has confirmed that such attacks are occurring, prompting users and organizations to update their GitLab installations.













