Note: I’ve gone ahead and updated the featured image, so it doesn’t seem like this has something to do with Discord “directly”. It was not my intention to leave an impression like that, but this still affects every single Discord user who was using the Discord.io service!
An unidentified individual has listed the data of 760,000 Discord.io (the site is dead at the moment, so you can see an Archive.org snapshot here) users for sale on a darknet forum. This discovery was brought to light by the “Information Leaks” Telegram channel, associated with the Russian service for tracking vulnerabilities, data leaks, and monitoring fraudulent online resources.
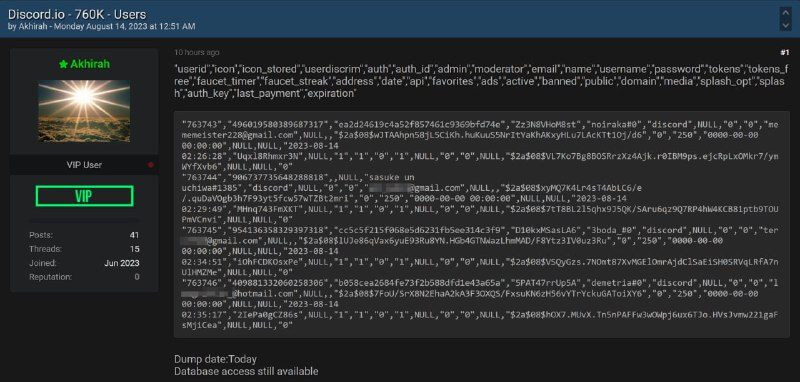
For clarity, Discord.io is/was a platform that allows you to create custom, personal Discord invites. The offered database comprises details like email addresses, hashed passwords, and other user-specific data.
Update (8/15/2023): A spokesperson from Discord has responded to my email with the following,
Discord is not affiliated with Discord.io. We do not share any user information with Discord.io directly and we do not have access to or control of information in Discord.io’s custody.
We are committed to protecting the privacy and data of our users and encourage our users to enable Two-Factor Authentication (2FA) to help keep their accounts protected, and consider SMS Authentication.
Additionally, we have revoked the oauth tokens for any Discord user that has used Discord.io, so that app can no longer perform actions on behalf of those users until they re-authenticate.
Overnight, a few other publications picked this up and spoke with the hacker (Akhirah), who said that his reasoning behind hacking Discord.io is that they enable illegal and harmful content and that the breach wasn’t about “making money”.
Nevertheless, now that Discord (the official app) has confirmed that the keys are revoked, the only thing you need to do is check your passwords and get 2FA enabled.
Discord.io team has now confirmed that the breach is real; an update is added at the bottom of the article!
To vouch for the authenticity of the data, the seller presented a sample which was then reviewed by cybersecurity experts. Their evaluation confirmed that the sample logins are genuine, matching real Discord users. And just to make it clear – genuine, as in the corresponding email addresses from the leak, were verified to be associated with real Discord accounts through several password recovery tests.
The implication here is that malevolent parties can exploit this data for phishing schemes, spamming, or other deceptive undertakings.
This does look to be real, though. I tried reaching out to the Discord.io team on their Discord server, and two minutes after joining, every single channel got manually deleted.
For users of the platform, the advisable course of action is to promptly change passwords and activate two-factor authentication on their accounts to bolster security.
Discord.io team confirms the breach is real; here’s what you need to know
The team behind Discord.io has officially confirmed the data breach. In a detailed statement on Discord, they provided a comprehensive account of the events that led to the breach, what data was compromised, and the subsequent actions they’ve taken.
Timeline of Events:
- Monday, August 14, 2023, 12:51 AM CET: A preview of the Discord.io user database appears on BreachForums.
- Monday, August 14, 2023, 4:30 PM CET: Discord.io team becomes aware of the breach.
- Monday, August 14, 2023, 4:36 PM CET: The breach’s legitimacy is confirmed.
- Monday, August 14, 2023, 4:40 PM CET: All Discord.io services commence shutdown.
Data Compromised in the Breach:
Non-Sensitive Information:
- Internal user ID
- Avatar details
- User status (e.g., moderator, admin, has ads, banned, public)
- Coin balance and current streak in the free minigame
- API key (relevant for a limited number of users)
- Registration and last payment dates, including premium membership expiration
Potentially Sensitive Information:
- Usernames, either from signup or the current Discord username
- Discord ID
- Email address associated with the account
- Billing address (pertaining to a select few users who provided this before the adoption of Stripe for payments)
- Salted and hashed passwords (mainly concerning users prior to 2018 when Discord.io began exclusively using Discord for logins)
Data That Remained Secure:
- Anything not explicitly mentioned in the compromised list.
- Payment details, which are securely stored with partners Stripe and PayPal.
Further Actions & Notes:
- All existing premium subscriptions have been canceled, with the team set to contact subscribers individually.
- As of their last update, the Discord.io team hasn’t established contact with the culprits nor discerned if the database has been shared with the public.
- A list of servers that once used Discord.io’s service has been made available, though it might contain outdated or inactive links.
- Users wishing to get in touch are encouraged to send a helpdesk request, with “Support” for general queries and “Admin” for sensitive matters. Given the gravity of the situation, the team cautions that they might not be able to address every message but appreciate user patience and understanding.













